Category: User Provisioning
-

ServiceNow Knowledge15 Looks to a Service Management Future
ServiceNow Knowledge15 focuses on fast easy enterprise-grade. In watching Frank Slootman, ServiceNow CEO and the Knowledge15 keynote speakers, you really do glimpse the future. The future of "Everything as a Service." For most enterprises, service management represents the state of operations in 2020. For some, particularly small and medium sized business, service management represents operations…
-

Killer Skills for an Identity and Access Management (IAM) Project
Red hot identity and access management skills. While working with a variety of companies who strive to improve their identity and access management program, I find that the most successful organizations have resources involved throughout the project that possess unique skills. It takes more than just IT project management and leadership skills to be an…
-

Building a User Community and Loyalty through Customer Support Services
Means “Use Your Community” In my previous blog, I wrote about the importance of hiring support professionals with strong communication skills. I indicated a support professionals’ written and verbal communication skills are as vital to successful support operations as their technical capabilities. Particularly, your support staff’s verbal and written skills are essential when interfacing directly…
-

2015 Identity Management and IT Security Predictions
2015 Top identity management trends. 2015 ushers in the age of identity management authentication. With compromised systems reported by Target, Home Depot, EBay, Neiman Marcus, and Goodwill, 2014 is remembered as the "year of the retail breach". In 2015 every industry becomes a target, every identity a vulnerability, and every app a potential host. As…
-

Go to the EDUCAUSE Conference Even if You Can’t
Attend the EDUCAUSE Conference online. Next week, the 2014 EDUCAUSE Conference showcases new instructional technology products, innovative educational services, and leadership best practices. With more than 250 exhibitors, four days of presentations, hot topic panels and a start-up alley, the event provides an opportunity to see how others address the key issues and challenges in…
-

Identity Management Already Crossed Geoffrey Moore’s Latest Chasm
With identity management, business users were always the focus. When Geoffrey Moore, first wrote his book, "Crossing The Chasm" in 1991 it became an instant success among marketers, and remains so today. They resonated with the deep gap in customers and companies who are willing to try any new technology and those who felt they…
-
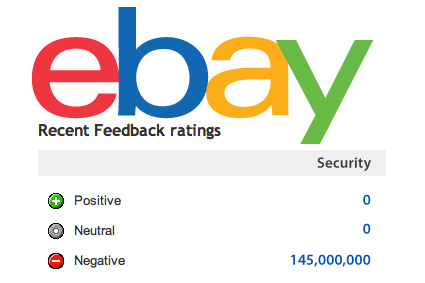
EBay Privileged Account Management Auction
eBay privileged account management feedback. I must confess. I am a little surprised by the media’s response and coverage of the eBay information security breach where hackers gained access to the personal data of 145 million customers over a four month period. During this time, cyber criminals accessed a database containing customer names, their email…
-

LANDESK Interchange 2014 an Educational Event for IT Experts
Learning that happens at LANDESK Interchange won’t stay in Vegas. With LANDESK Interchange 2014 a few days away, I could not be more excited about this year’s sessions, workshops and roundtable discussions. As someone involved in both education and marketing, I must confess I find conferences with an educational focus of greater value than their…
-

EDUCAUSE Security Professionals: Meet Me in St. Louis, Louie
At the EDUCAUSE Security Conference, the force is strong. The 12th Annual EDUCAUSE Security Professionals Conference 2014, drew from two audiences this week in St. Louis. Over 400 security staff, IT staff, privacy officers, and others from the higher education community with an interest in security and privacy were there in force—and a multitude of…
-

Avatier Packs Major Identity Management Changes into AIMS 9.5
Liftoff! This month the company launched the latest version of its Avatier Identity Anywhere (AIMS) providing several significant additions. AIMS 9.5 now includes SMS self-service password reset, a new patented approach to increased IT store intelligence, and revolutionary risk mitigation throughout. Enterprise Password Management AIMS’ Password Management module now features SMS two-factor authentication without requiring…
-

How an Identity Manager Stops Edward Snowden Administrators
Privileged whistleblower. Since Edward Snowden’s release of over 1.7 million classified NSA documents, trusted identities and privileges require re-examination. While opinions regarding Snowden range from traitor to Noble Prize winner, his actions delivered a wake up call to IT leaders. As an IT security professional, whether you support or abhor Snowden’s actions, you must take…
-

Identity Management and IT Security Practices to Prevent Target-like Cyber Theft
IT security alerted. Last Friday near the end of day I thought I would speak to one of our engineers about this blog topic. Coincidentally, 5 minutes into our conversation, he received an alert indicating unusual resource consumption on our blogging server. Upon examination, someone accessing our login page from a server in New Jersey…
-

Have A Hacker Over For The Holidays
Cyber Carol ‘Twas the night before Christmas and all through the house, many creatures were stirring while holding a mouse. Their stockings were hung by computers with care, in hopes that their breakins soon would be there. It turns out you don’t really need to invite a hacker over for the Holidays… they’ve invited themselves.…
-

Avatier at the Gaming & Leisure Roundtable: IT Automation Makes Life Easier
Gaming & Leisure challenges. Recently we had the opportunity to attend the Gaming and Leisure Roundtable in Las Vegas. The event, put on by the Gaming and Leisure Magazine, is unique in that CIOs and other C-level executives from gaming organizations around the world gather at a forum to speak candidly about key issues and challenges.…
-

IAM and User Provisioning: Conquering the Convergence of Customer Concerns and Compliance Management
User provisioning mountain top. Banking, government and health care — how are these market sectors alike? For starters, organizations operating in these verticals possess deep and comprehensive personal information from their customer bases. Second, regulatory compliance requirements are intensive and the IT audit cycle is frequent. Third, people are concerned about and paying attention to how…
-

User Provisioning Unraveled — Untangle the Mess with Access Management Integration
User provisioning and access management system. With scores of folks navigating your networks, is your IT department keeping a handle on who’s accessing proprietary data? There are so many user groups needing just a small sliver of access — employees, channel partners, contractors, vendors, customers and prospects — it’s virtually impossible to keep it all…
-

Justin Bieber – a reason for effective automated user deprovisioning
Automate celebrity user provisioning and de-provisioning. As a musician and an information security professional, I personally wish that de-provisioning could apply to Justin Bieber. I am pretty sure that most professionals in the real world have the same feelings I do based on recent media attention and online comments, so hopefully everyone appreciates the ability…
-

Become the Identity Business "Man of Steel" with IT Service Catalog User Provisioning Software
Provisioning business users with super power. Any business user can be a “Man of Steel” and manage their own accounts to streamline operations, lower costs and better service. When you automate your IT service catalog user provisioning software, you’re able to grant your users the capability to safeguard your security through permissions specific to each…
-

Electronic Medical Records: Why Health Care Organizations Must Address User Provisioning Before Going Digital
Healthcare IT user provisioning. There’s a significant push in the medical industry for creating electronic medical records and for good reason. When there’s a user provisioning solution for integrating and connecting systems while securing access for the right people to obtain a patient’s records, health care practitioners can provide a better care experience. And when records…
-

The Corporate IT Store: NOT your Father’s ITIL Service Catalog
ITIL Service Catalog horsepower. Like my father before me, I earn my living, at least in part, as a writer. Unlike my father, however, most of my writing depends upon my knowledge of technical aspects that would have been well beyond his comprehension. That’s not a knock on his intelligence; it’s merely acknowledgement that times…
-

Harry Potter and the Gartner Identity Management Magic Quadrant
Riddikulus! What’s so "magic" about the Gartner Identity Management Magic Quadrant? The Identity & Access Governance Management Magic Quadrant was just released and it’s not a "wand waver" by any stretch of the imagination. And that’s the point. If you go with the Leaders in this quadrant, are you really getting any imagination, creativity, or innovation or are…
-

ISACA Cloud Security Blog
ISACA addresses critical issues head on. Cloud security continues to be a hot topic in the information security world, and a recent ISACA webinar reaffirmed the fact that identity management is more critical than ever as services shift from on-premise to cloud-based solutions. One particular presentation stood out during the ISACA webinar for the three aspects…
-

IT Service Management: Five Features of a Road Less Traveled
IT savings add up. There are many paths organizations could take to achieve optimal IT Service Management (ITSM). While the necessity of a refined process for ITSM may not be apparent immediately, its essential nature in handling Identity and Access Management (IAM) issues becomes glaringly apparent as the help desk becomes more saturated with requests.…
-

Data Problems? How to Overcome Automated User Provisioning Obstacles
Stride over user provisioning hurdles. When embarking on an identity and access management project, the accuracy of data and data transmissions is paramount to enable automated user provisioning. Data residing in HR systems and core directories should be carefully reviewed prior, during and after an IAM solution is put in place. Never underestimate the criticality…
-

‘No Sweat’ User Provisioning Software for Identity and Access Management… Even in Winter
Automate identity and access management user provisioning. Winter is not generally associated with people sweating, even in Duluth, Georgia, where high temperatures today were slated to dip into the 40’s. If you’re one of the top 100 hospitals in the United States, though, and handle more than 11,000 transfer requests per quarter, nobody would blame…
-

Cyber Security: How to Cover Your SaaS
Reach for SaaS cyber security. While attending various conferences, roundtables and other information security gatherings, a common theme that often presents itself is the concern over security of software-as-a-service (SaaS) vendors. Another common theme seems to be that IT cyber security teams are either very confident with how they are managing this particular “cloud” risk…
-

Solid Cyber Security Takeaways from ISSA Chapter
ISSA IT security experts gather. I recently attended my local ISSA chapter meeting, and there were some key takeaways relating to successful cyber security management practices amongst the group. In order to enlighten blog readers, I thought I would highlight some of the successful practices to hopefully inspire others out there to up their game.…
-

Top 10 Cyber Security Software Hacks on Santa’s 2012 Most Naughty List
Top holiday cyber security hacks. Here we are, one year older and one year wiser when it comes to cyber security software, but unfortunately it seems those who mean to undermine cyber security systems have also grown. While there seemed to be a lot more high profile attacks on government and private business in 2011,…
-

Gartner Identity and Access Management Summit Wraps Up
Gartner Identity and Access Management insights. It was quite a week in Las Vegas for the annual Gartner Identity and Access Management (IAM) Summit. While Avatier may not have been exactly a household name going into the conference, we certainly did our part to spread the message about the innovative ways the company is taking…
-

Using Identity Access Management Software to Secure the Whole
Identity and access management lockout. Webster’s defines “holistic” as “relating to or concerned with wholes or with complete systems rather than with the analysis of, treatment of, or dissection into parts.” Nevertheless. While addressing “the whole” as opposed to its parts seems like a wise plan, in society we find that industries are slow to…
-

A Corporate Cyber Security Risks Wish List
IT security greeting. God rest ye merry IT men, let nothing you dismay; Remember hackers’ prime season began on Black Fri-day… While Avatier shows off its new access certification tool, Compliance Auditor, at the annual Gartner Identity and Access Management (IAM) Summit next week, a special group of people around the world is busy preparing…
-

After Turkey Day Avatier Goes for "All the Fixin’s" at Gartner Identity Management Summit
Gartner IAM Las Vegas. This week, hearts and minds across the U.S. are focused on the upcoming Thanksgiving holiday and all that it offers — giving thanks, being with family and eating lots and lots of turkey with all the fixin’s. While we at Avatier join others in these thoughts, in the backs of our…
-

Top 5 Cyber Security Access Certification Measures to Rock the Online Vote
Access certification and the future of voting. Last week our country voted to keep a president and change our congress… and not a single shot was fired in anger to do it. I’ve been enthralled by the seamlessness of this process since a very young age. By 9 years old, I was already pouring over…
-

KuppingerCole ‘Compass’ Points to Identity Management Software Innovator
KuppingerCole recognizes innovation. Innovation is one of Avatier’s core values and a key to its cyber security strategy in identity management software. But it’s one thing to tell people you’re innovative; it’s another thing all together to have an expert in the identity management software field confirm it. That’s what happened last week when KuppingerCole,…
-

Identity and Access Management (IAM) Integration Reaches for the Cloud
IAM in the cloud. I confess that I’ve been around the Tech industry long enough (i.e., the 1990’s) to recall when "working from home" was not an easy thing to do. For most companies back then, when an employee wanted to work from home he or she usually did not have a way to connect…
-

Reviewer Calls Avatier’s Identity and Access Management Software Suite ‘A Remarkable Offering’
Best identity manager. SC Magazine, one of the most highly regarded publications covering the IT cyber security space, recently published a review of Avatier’s Identity and Access Management (AIMS) Software Suite. The suite, which is Avatier’s main identity and access management software product and incorporates products for user provisioning, password management, governance risk compliance, and…
-

A Celebration of Identity Intelligence and Integration
Pop the corks! It has been my experience most successful cyber security measures and platforms are those run "in the background"; applications so seamlessly integrated into the overall system the only time a user notices them is when he or she is entering login information. Even then, most users give nary a notice because the…
-

Do It Yourself (DIY) IT Compliance Management
Don’t do it. Does everyone remember when Full Service gas stations were the norm, and Self Service was rare? Would you prefer to go back to Full Service filling stations, or are you happy having the ability to manage the process on your own? On a similar topic, do you prefer to pay at the pump with…
-

5 Ways Companies Can Kick Identity Management Security into SaaS
Identity management SaaS is no joke. When it comes to growth in IT systems, we usually think problems like identity management security and enterprise risk management compliance increase with technology advances. According to Gartner Analyst Guy Creese, however, despite 68% of U.S. companies and 80% of Asian companies saying they plan to expand their Software…
-

There is No "One Size Fits All" Solution to Cyber Security Incident Response
Cyber security incident response on shaky ground. When speaking of “an ounce of prevention” is worth more than “a pound of cure” it is unlikely that you will find many who disagree with the sentiment and the IT world seems to have taken this concept as its personal mantra. New technologies and system updates are…
-

Empowering Users Is More Than an IT Service Catalog Fad
An ‘actionable’ IT service catalog. It’s been fascinating over the years to watch the network architecture pendulum swing back and forth. First, networks were organized around a mainframe with what were then called dumb (now more respectfully referred to as thin) clients. Then we moved into the client/server era, where users revolted at the dictatorial manner…
-

5 Key Reasons Enterprises Deploy Robust Identity and Access Management Software Solutions
Enterprise identity and access management automation. I write so frequently about specific issues, features and products related to identity and access management software, I sometimes lose the forest through the trees. It’s important to step back and think through periodically exactly what IT teams are attempting to accomplish when they deploy an identity and access…
-

Provisioning User Directory Cleanup
User provisioning directories scrubbed. Before diving into an identity and access management (IAM) project, doesn’t it make sense to solve your directory issues for provisioning users first rather than trying to hide them with identity access management customization Issues with accounts, unused groups, naming conventions, policies and simply having too many directories all equate to a…
-

Forget the Wide Net — Spear Phishing is the Next Big Cyber Security Threat
Cyber criminals spear phish. We’ve all been warned about cyber security phishing, and many of us have received emails sent by cyber criminals that link back to phony branded websites requesting personal data. We’ve been told to be wary of suspicious “from” addresses, spelling errors and unfamiliar URLs, and subsequently we’ve become significantly savvier —…
-

With Self-Service Group Management Birds of a Feather Rarely Need to Stick Together
Self-service group management alignment. Unlike flocks where the group stays together while on their way to migrate South, groups inside companies are constantly changing. They pop up regularly for long and short-term projects, add or delete members on a regular basis and always have, hopefully, a sunset clause. To set up manual rule based group management…