Category: Misc
-

Mastering Incident Response Planning for NIS2 and DORA: Prepare to Respond Swiftly
Effective incident response planning is a critical component of any organization’s cybersecurity strategy.
-

Maximizing Cybersecurity through Effective User Lifecycle Management
Effective User Lifecycle Management is a critical component of a robust cybersecurity strategy.
-
Empower Your Security: Avatier at COMMON POWERUp 2024 | May 20-23 | Ft. Worth, TX
Join Avatier at booth 504, COMMON POWERUp 2024, May 20-23 in Ft. Worth, TX, and discover innovative IT security and identity management solutions.
-
Passwords Are Far from Dead: The Increasing Need for SSO
Rumors of the death of the password have been greatly exaggerated. In fact, passwords have become more important than ever with the proliferation of remote workers and today’s digital workforce. Despite predictions about biometrics, token-based encryption, and other authentication strategies, using secure passwords will be the most common means of protecting digital assets. What does…
-

How To Manage Smart Home Device Security Risks
Smart home security risk is no longer an issue for consumers and households alone. More and more people are working from home, so home electronics may impact corporate networks. In addition, some smart home devices are portable, so they may be brought into the workplace. As a result, IT professionals need a process to assess…
-

Can You Prove That You Are ISO 27001 Compliant?
ISO 27001 compliance is one way to determine if your organization is keeping up with industry standards. It is a complex standard, so achieving compliance is not a simple process. Before we go further, let’s unpack why ISO 27001 compliance is a worthwhile goal. Three Reasons Why ISO 27001 Compliance Matters For Your Company There…
-

How Avatier Mobile Works with Apple Face Recognition Login (and same with Google)
Your users demand convenience, even when it comes to security. That’s why Avatier has developed facial recognition capabilities using mobile apps. Whether your organization uses Android or iOS devices, you can get facial recognition capabilities quickly using the built-in features on these devices. Let’s start with Avatier’s Android Apps. Android: Avatier Identity Anywhere and Avatier…
-

How To Speed Up Password Management
How long does it take to do effective password management at your company? As a critical line of defense in your company, passwords need to be managed well. You’re one weak password away from a major security incident. On the other hand, you are juggling different projects and activities in your cybersecurity program like incident…
-

Avatier vs CA Technologies
Considering a choice of Avatier vs. CA Technologies for your identity and access management needs? If you have already developed your shortlist for products, it is time to look at features and capabilities so you can make a smart choice. Specifically, you will see a comparison focusing on Layer7 SiteMinder vs. Avatier Single Sign-On. 1)…
-

Avatier vs Microsoft Azure AD
You’re considering Avatier vs. Microsoft Azure Active Directory. Which identity management solution is right for your needs? It’s not as simple as choosing a familiar brand. You need to take a closer look at some of the specific capabilities. Use this product comparison to develop your software solution shortlist. Once you have a few products…
-

How To Design A Role Based IT Security Training Program
Your people can be your greatest threat or your greatest IT security weakness. Reinforcing the importance of IT security regularly is helpful. However, you also need to equip your employees with the skills and knowledge to make smart decisions. Without robust IT security training, your staff is more likely to make security mistakes. Now, here’s…
-

How To Respond To IT Security Audit Finding
Do you like to hear from your auditor? Let’s be honest: few managers look forward to receiving IT security audit findings. If you feel bad for avoiding these audit reports, you’re not alone. These reports not only require work to address, but they sometimes make you look bad. That’s the traditional mindset when it comes…
-

How To Prevent IT Security Department Burnout
IT security failure is an ever-present danger. New threats and ways to attack your organization are constantly being developed. Defending against these threats is a tough challenge for companies across the world, even small firms. You can get an early warning of your vulnerability to a security failure by monitoring and preventing IT security department…
-
The Top Multi-Factor Authentication Myths and Misconceptions You Need to Know About
You’ve heard of multi-factor authentication, but you haven’t started using it across your organization yet. If you’re skeptical or worried about adopting multi-factor authentication (MFA) at your company, you might have out-of-date information about what it involves. Or, you might believe one of these myths and misconceptions. Let’s set the record straight right now. Myth:…
-

How to Stop Identity And Access Management Risks from Growing Like Weeds
There’s a specter haunting IT departments around the world: increasing identity and access management risk. Left unchecked, this trend will quietly raise the impact and likelihood of an IT security event. Unlike other corporate problems such as fraud or high employee turnover, detecting and controlling this risk is difficult. There’s a way to make it…
-

How to Protect Executives with MFA Security
As corporate leaders, your executives are highly visible representatives of the organization. The public knows the names of your executives and what roles they play. Likewise, hackers know the same information. Instead of taking the long path of breaking into multiple systems, a focused attacker merely needs to impersonate one of your executives to cause…
-
Five Ways to Boost Your Cybersecurity Incident Response Capability
Cybersecurity incident response is the best of times and the worst of times for security professionals. Without a doubt, it’s incredibly stressful. You face difficult questions from senior management, customers, and sometimes governments. That`s the painful side of incident response. On the other hand, it’s exciting work! Walking into work, you know that your contribution…
-

5 Ways Apollo Saves Time for IT Security Operations
Keeping up with the constant threats and vulnerabilities in cybersecurity is a daunting task. When everything goes well, meaning no hacks or system failures, you get no recognition. When an attack takes down company systems, you face the pressure and stress of answering tough questions about how you let this happen. Unfortunately, there’s never enough…
-

What is DevOps?
Every week, new releases for apps come to the market. Every quarter, there are new startups launching that are keen to disrupt (meaning steal market share!) established companies. The old way of doing business just isn’t going to cut it any longer. Some big firms choose to acquire small firms to keep pace, but that’s…
-

Announcing Identity Anywhere: What It Means for IT Managers, Developers, and Security Pros
Do you use Docker Containers but keep having to improvise identity management solutions? That era is over. Avatier has become a Dockers Partner. We have the first security and identity management product built on Docker Containers. We’re committed to helping Docker Container users manage and reduce their cybersecurity risk. Now, what does this announcement mean…
-

How Do Avatier and Okta Compare?
Identity Access Management (IAM) is an increasingly important aspect of business technology, helping advance security by providing the tools needed to manage system access and security credentials. In fact, the current climate of rising IT security concerns paired with increased movement to cloud computing has led to projected a 12 percent growth for the IAM…
-

6 Ways to Make the Most of Homeland Security Week 2018
National security threats are continually evolving. In the past, there were simply armies, missiles, and tanks, which are bad enough. Today, adversaries can use hacking tools to pursue their goals. These hacking tools and methods are becoming cheaper and more powerful each year. To stay ahead of the latest threats, you need to attend Homeland…
-

Create Your Identity Management Shortlist Using These 6 Traits
Fix your identity management processes and systems and your entire cybersecurity program will improve. Once you get into the details, it quickly becomes evident that improving identity management is quite difficult. If you miss one new hire or one system, your entire system can fall apart. How do you overcome identity management problems and minimize…
-

How To Mature Your Container Management
You started to use containers for the productivity benefits. We get it. Containers are an excellent way to remove roadblocks from developers and reduce your technology costs. However, they don’t manage themselves. If you lack a holistic process to handle containers, you may be adding cybersecurity risk to your organization without knowing it. What’s Container…
-
Defining Multi-Factor Authentication: What It Is and Why You Need It Now
You may have heard of multi-factor authentication, but never got a clear definition of what it is. Stay tuned, and you will find out the definition and what this authentication process can do for you. Ultimately, you want more than information — you want a way to solve your security problems. You will get both.…
-

Secure Your Digital Systems With Assisted Updates And Migrations
Windows Server Migration Database Migration Assisted Upgrade Did you know that using outdated technology exposes your company to significant security risks? Because legacy software can no longer be patched or updated, systems that use older technology will not be secure against today’s current threats. In fact, 44% of data breaches are caused by known system…
-

How to Tell if Your Vendor is a Thought Leader
Why We Love to Buy From Thought Leaders There’s a critical distinction between experts and thought leaders when we decide to buy. An expert may know their subject well. If they do not publish and share their expertise publicly, there is no way for us to get to know their expertise. When you buy from…
-

The 8 Factors Successful Identity Management RFPs Always Have
What is an RFP? RFPs (request for proposals) are a widely used procurement process in large companies and government. Generally, RFPs in technology purchases also give the vendors latitude to propose creative solutions as well. RFPs are widely used in government procurement where regulation and fairness concerns are top of mind. If this document is…
-

How Supply and Demand Sets the Help Desk Budget
A Day in the Life of Your Help Desk You walk into the office, get your coffee, and open the phone lines. By 9:10am, the help desk phone queues are full. Help desk work is tough because you have to keep smiling and helping people even when they are upset about having to wait in…
-
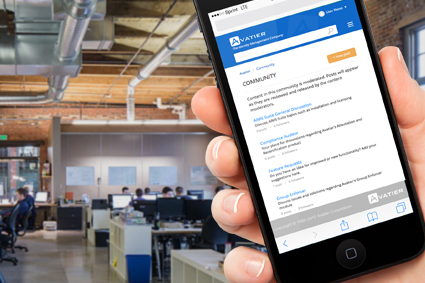
Avatier Launches an All-Inclusive Avatier Community Portal
Avatier, the global leader in Identity and Access Management (IAM) software, is excited to announce the premiere of Avatier Community. This online portal puts all of our tools and resources right at our customers’ fingertips. It provides Avatier customers with exclusive access to an expanded knowledge base, a forum to connect with other community members,…
-

Password Management + DUO = How They Work Together
Avatier now offers integration with DUO for multi-factor authentication (MFA) to Password Management. In addition to answering security challenge questions, users can now select from one or more multi-factor methods to further secure a password reset operation. The integration gives Avatier users the flexibility to use DUO or use Avatier’s existing MFA technology.
-

Avatier Group Self-Service Eliminates your Enterprise Risk Management Cyber Security Exposure
It’s time to put the trusted group accountability in the hands of business owners, rather than IT. Avatier Group Self-Service lets business users request membership while workflow automation controls changes and applies cyber security software audit controls. Let business users request groups to add to your systems without impeding IT. Automate workflow and establish group…
-

Biometrics in Movies Sci-Fi Security
Facial recognition used to just be for science fiction. Eye sensors and voice scanners used to only be something we’d see in the movies. But these biology-based security systems from science fiction are no longer just futuristic dreams. They are now the reality of maintaining security. Let’s revisit some examples of biometrics in movies and…
-

Hartford HealthCare Sees a Reduction in Help Desk Staff by 30% Within Two Years Using Avatier’s Password Management
Hartford HealthCare is Connecticut’s most comprehensive healthcare network. The fully integrated health system includes a tertiary-care teaching hospital, an acute-care community teaching hospital, an acute-care hospital and trauma center, two community hospitals, the state’s most extensive behavioral health network, a large multi-specialty physician group, a regional home care system, an array of senior care services,…
-

Avatier Password Management Now Offers Safe and Secure MFA Biometric Solution
Avatier Corporation announced at the Gartner Identity & Access Management Summit 2016 in Las Vegas, NV the release of Multi-Factor Authentication (MFA) Biometrics for its Password Management solution. Password Management is now more secure than ever with the introduction of MFA Biometrics technology. Users can authenticate their identity and securely unlock account, reset and synchronize…
-

Webster Bank Saw Immediate Results with a 70% Decrease in Password Reset Requests
Webster Bank was founded in 1935 by Harold Webster Smith. Growing from humble roots, Webster Bank has become the leading regional bank in the Northeast and offer a full range of financial services to their customers including personal, business, commercial and institutional banking. They expanded from Connecticut into neighboring states, and continually work toward expanding…
-

A Large Retail Company’s Help Desk Ticket Volume Reduced by 90% With Avatier’s Self-Service Password Reset Solution
Large retail corporations face many challenges in order to maintain a smooth operating procedure. The constantly-evolving environment of cyclical need for more employees during the holidays and a high turnover rate creates a nightmare for the help desk. In 2008, the Director of IT Security of one such retail company knew that he needed to…
-

U.S. Banks With Over $50 Billion in Assets Face New Demands to Shield Themselves From Cyber Hackers
Hacker groups are the organized crime of the cyber world. They are pirates calling parley with one another, thriving in a virtual treasure-trove of shared information. Their success stems from a willingness to share their secrets and the tricks of their trade with each other. Bank Security Protection against hackers is a relatively new idea.…
-

Cox Enterprises Now Does More Complex Tasks at a Lower Cost with Avatier’s Password Reset Solution
Cox Enterprises was founded in 1898 by James M. Cox and is based in Atlanta, Georgia. They are a juggernaut in the communications, media, and automotive services industries with major brands including Kelley Blue Book, Autotrader.com, Savings.com, and Valpack. Vic Chandar, a Senior Manager at Cox Enterprises, knew that their key goal was to reduce the…
-

Reduce Help Desk Calls by 30% with Avatier’s Self-Service Password Reset Management Solution
Users have a multitude of passwords to recall, often due to the fact that password security requirements are not universally the same. There’s the simple go-to password, the slightly more complicated password, the one that passes most security requirements… and then there’s the password that’s asking for your social, first born child, the national anthem,…
-

Intuitive Surgical’s User Account Creation and Setup Across All Systems Dropped to 5 Minutes with AIMS
Intuitive Surgical was founded in 1995 and headquartered in Sunnyvale, California. They developed the revolutionary da Vinci® system to assist surgeons in minimally-invasive robotic surgery. In 2003, they merged with rival Computer Motion and subsequently grew at an unprecedented rate. Today, they remain a gold standard in the industry and the global leader in robotic-assisted…
-

Gartner Identity and Access Management for Third Parties
Limiting third party security risks. Today’s enterprise requires IT organizations to fully engage external users. This audience includes such as contractors, business partners, vendors and suppliers. The Gartner Identity and Access Management (IAM) for Third Parties webinar offers best practices for managing third-party identities and access control. Lori Robinson, Gartner Research VP, relates challenges in…
-

The Panama Papers Represent Failed Leadership and Information Security Controls
Hacktivist expose an information security truth. The Panamanian legal firm Mossack Fonseca’s leak exposes a systemic security lapse. In revealing the obscenely wealthy businessmen and heads of states that used the firm to avoid taxes, the Panama Papers brings security awareness to the forefront. By releasing 2.6 terabytes of data, it highlights damage caused by…
-

Verizon Data Breach Scenarios Stress Identity Management with Multi-Factor Authentication
Strong authentication is cybersecurity’s best defense. The Verizon Data Breach Digest, Scenarios from the Field summarizes over 500 cybersecurity investigations. The Digest informs organizations about security attacks, the methods used and victims. It shows a limited number of techniques describe most incidents. In fact, twelve scenarios represent over 60% of all investigations. The report groups…
-

Last Year’s 25 Worst Passwords Reinforce Strong Passwords Matter
Enterprise security begins with strong passwords. Passwords are the most common way to authenticate access. At home, on the job, and using social networks, applications require passwords. As the systems you log into increase, you assume greater risk. This is true for one reason. Most passwords are weak and in all likelihood, you use them.…

