Category: IT Risk Management
-

Verizon Data Breach Scenarios Stress Identity Management with Multi-Factor Authentication
Strong authentication is cybersecurity’s best defense. The Verizon Data Breach Digest, Scenarios from the Field summarizes over 500 cybersecurity investigations. The Digest informs organizations about security attacks, the methods used and victims. It shows a limited number of techniques describe most incidents. In fact, twelve scenarios represent over 60% of all investigations. The report groups…
-

Extended Enterprise Security Risks Countered by Access Management
No end to extended enterprise security risks Management of assets, access requests, and user identities continues to change. No longer are employees the only ones accessing enterprise systems. No more are desktop computers and laptops merely used. A gamut of professionals engage multiple organizations. They use their own equipment to cross-different firewalls. They may even…
-

2016 Cyberthreat Defense Report Points to Identity and Access Management as Essential to Controlling IT Security Risks
When IT security fails, blame the users. The Cyberthreat Defense Report shares among the IT security community information on how organizations are fairing. Of the 1,000 survey participants, 40% were from North America, 30% from Europe, 20% from Asia Pacific, and 10% from Latin America. For respondents, 40% were senior executives; 25% focused on security…
-
Self-service Password Reset Authentication Options
Watch Password Management Phone Reset Video Authentication is near. Self-service password reset lets users reset passwords without help desk assistance. As a result, help desk no longer needs to verify users over the phone. Instead, users can confirm their identity through a variety of options. When describing options, enterprise password management vendors focus on the…
-

Last Year’s 25 Worst Passwords Reinforce Strong Passwords Matter
Enterprise security begins with strong passwords. Passwords are the most common way to authenticate access. At home, on the job, and using social networks, applications require passwords. As the systems you log into increase, you assume greater risk. This is true for one reason. Most passwords are weak and in all likelihood, you use them.…
-

2016 Identity Management and IT Security Predictions (continued)
IT security predictions and identity management solutions for 2016. Our initial IT security predictions point to fewer incidents producing greater damage in 2016. This trend begs for an explanation. With fewer breaches costing more, security attacks take on enhanced sophistication. As BYOD and cloud apps reach the workplace, organizations find themselves unprepared. Similar to our…
-

2016 Identity Management and IT Security Predictions
IT security predictions and identity management trends for 2016. Last year, security breaches became a boardroom topic. In 2016 leading organizations recognize identity management as a business enabler. When security breaches’ occur, identity and access management (IAM) contains the cost and limits damage. To mitigate risks, organizations must shift their security focus to detection and…
-

Gartner IAM Six Principles of Resilience
Identity and Access Management (IAM) empowers an enterprise to build resilience. Fully charged, we’re back from the Gartner IAM Summit in Las Vegas. Looking to the New Year, it seems appropriate to comment on risks. The keynote, Ant Allan, spoke on “Managing Identities and Access in a Digital World." Speaking frankly, the Gartner IAM Summit…
-

Charlie Sheen A HIPAA HITECH Tragedy
Identity management automation peace of mind. I actually feel sorry for Charlie Sheen. I’m sure Charlie has his character flaws along with excessive fame. I am also certain he is entitled to his medical privacy. When you consider, people in his private circle blackmailed him. Most would agree he is a living tragedy. For all…
-

Time to Expire Phishing Strikes and Security Breaches
Detect cyber attacks before they score. In studying timelines of enterprise security breaches, organizations must shift their focus. Rather than firewalls and perimeter defense, the real damage occurs once inside. The longer cyber thieves remain unexposed the greater the cost. The 2015 Verizon Breach Report indicates 45% of attacks are initiated by phishing. As a…
-

Gartner ITxpo Showcases Identity Management Prevention Controls
Identity management takes center stage at this year’s Gartner ITxpo. The Gartner Symposium ITxpo tends to be broad and scattered with numerous IT security and risk management solutions. Generally, at the Gartner ITxpo, participants do not naturally see the connection between identity management and information security. At this year’s 2015 ITxpo, the roadmap to security…
-

KuppingerCole Digital Risk and Security Awareness Survey Paradox
KuppingerCole is a leading identity focused information security analyst company. After reviewing KuppingerCole’s, Digital Risk and Security Awareness Survey, I have a goal. In joining my associates with improved cyber security awareness, I must confess. I am not in the report’s minority, where I should be. As expected, most IT professionals see risks and threats…
-

MLB Steps Up to Identity Management Big League
Major League Baseball ushers in a new era of cheating. Baseball, known as America’s Pastime, reflects our national identity, culture and values. The 1967 Major League Baseball (MLB) World Series featured the St. Louis Cardinals. The Series remains one of my earliest memories. On a tree swing in the backyard, I listened to the game.…
-

Top Identity Management in the Cloud Enterprise Applications
Most frequently requested enterprise cloud apps Let’s all agree. Identity and access management is core to IT security. Administration of software access and an individual’s credentials embody fundamental IT operations. Today, user management requires governing access to cloud and enterprise applications alike. Experts project global SaaS revenue to top $106 billion next year. This number…
-

NSA Map Shows Chinese Government Cyber Attacks on U.S. Targets
Over 600 reported cyber attacks since 2010. In the movie, Tucker: The Man and His Dream, Jeff Bridges plays Preston Tucker. As an entrepreneur, Tucker failed in 1947 to change the automotive industry. As a visionary, he succeeded in advancing automobile design, manufacturing and safety. In one scene, Tucker delivers an impassioned speech to investors.…
-

Eight Identity Management Practices for Stopping State Sponsored Cyber Attacks on Washington
Identity management defends against state sponsored cyber attacks. Last week Leon Panetta spoke at the Gartner Security Summit. His topic related to preventing cyber attacks in 2020. The irony was not lost considering four days prior. The Department of Homeland Security (DHS) announced our government’s largest security breach. Initially, ABC News reported four million employee…
-

Speeding Up the Gartner Security Summit
Gartner Security Summit Keynote Leon Panetta The Gartner Security & Risk Management Summit 2015 in Washington DC was no snooze fest. Quite the contrary. It’s just I don’t usually plan for security threats five years in advance. I’m engaged today. With the event infogram, "By 2020, 25% of global enterprises will engage the services of…
-

Why Identity and Access Management is an Information Security Best Practice
Good habits make for information security best practices. When the CISO of a large organization calls and starts the conversation with “you’ll never guess why I’m calling”, usually I do have a pretty good idea of why they called. Something bad has already happened. Even though organizations claim to know the best security practices, it…
-

An IT Security Culture Deters State Sponsored Cyber Attacks
Time to develop a security culture. In previously criticizing the Anthem breach, I focused on preventative technologies. Clearly, identity and access management (IAM) makes cyber attacks difficult to launch. Equally crucial, IAM systems enable rapid remediation. They provide controls to automatically decommission compromised accounts, orphaned servers and passwords. During the Dropbox credential spoof, I highlighted…
-

Chart Your Path to Identity and Access Management Success with Risk in Mind
Identity and Access Management charter. Identity and Access Management (IAM) projects are generally executed with a focus on delivering operational improvements, cost savings and eventual long-term security enhancements. Today, I am questioning whether you can afford to be satisfied with a "long-term" goal of security enhancements with your IAM program when organizations are being attacked…
-

Simulations – Use Them Often and Everywhere for Information Security Improvements
Information security best practices. Practice makes perfect! This especially holds true in the world of information security where awareness and response capabilities must always be tested to prepare for and avoid breaches. Simulations of security events not only help you react and respond during an actual incident, they can also be used to proactively educate…
-

Identity Management Mitigates an Anthem Healthcare IT Breach
Anthem exposes healthcare IT vulnerability. When I initially read the Joseph Swedish letter taking responsibility for the Anthem information security breach, I found it refreshing. Upon finishing the message, I thought he should be fired. I mean. In a similar situation, who shouldn’t? More to the point, the third paragraph really got me: “Anthem’s own…
-

Cyber Liability Insurance Puts a Large Hole in the Corporate Wallet
Cyber liability costs. I was talking with a friend the other day and the cost of cyber breaches came up. Not so much the loss of reputation (which everyone faces), and the loss of sales, (which many face) and the loss of jobs (as Target executives faced)—but the cost of liability insurance assuming there is…
-

Risk Assessment Benefits, Best Practices and Pitfalls
Risk assessments clean up operations. This interview with Avatier CISO, Ryan Ward, speaks to the overlooked benefits of risk assessment. It recently appeared in Help Net Security and offers best practices for performing successful risk assessments, remediation, and professional development. What are some of the often-overlooked risk assessment benefits? Even though most organizations have a…
-

2015 Identity Management and IT Security Predictions
2015 Top identity management trends. 2015 ushers in the age of identity management authentication. With compromised systems reported by Target, Home Depot, EBay, Neiman Marcus, and Goodwill, 2014 is remembered as the "year of the retail breach". In 2015 every industry becomes a target, every identity a vulnerability, and every app a potential host. As…
-

Is Your Incident Response Plan Ready for 2015?
You must be ready to engage twenty-first century threats. From my past articles, you can probably tell that I like to preach about focusing on the basics of security management rather than the latest shiny security tool. Things like vulnerability management, identity and access management, security awareness, etc. all help lower risk and improve security…
-
The 12 IT Security Hacks of Christmas
Who’s putting coal in your IT security stocking? Although 2013 is remembered as the “year of the retailer breach,” in 2014, no industry is left out. With IT security breaches totaling over a half billion records in 2014, companies like Adobe, Ebay, JP Morgan Chase, Home Depot, AOL, NASDAQ and even Google joined the fold.…
-

What Will Your IT Security Get For The Holidays This Year?
IT Security gifts for the Christmas holidays. Happy Holidays! At least we’re all hoping they are going to be happy. With cybercrime and cyber terrorism on the rise, we’ll be lucky if we don’t get coal in our cyber stockings this year — especially if they already have cyber holes in them. According to a…
-

Continuity and Automation Stop an IT Security Saga
Don’t let life put IT security in a twist. Monday, 11:55 PM: It’s been a long day for Bob. He worked all day as an information security professional, and then, he entertained a large group of friends all evening while watching Monday Night Football. Tuesday, 6:00 AM: Slow to wake and feeling a bit under…
-

Chiming In at the College of Healthcare Information Management Executives CIO Forum
CHIME 14 CIO Forum for healthcare IT executives and leaders. Last week I had the opportunity to participate in the CHIME 14 CIO Forum in San Antonio, Texas. This year the College of Healthcare Information Management Executives (CHIME) hosted over 800 industry professionals from all areas of the healthcare field representing the largest forum in…
-

Risk Should Point to Identity Management Investments
Identity management improves security at a lower cost. My numerous years of information security leadership experience at large organizations have helped me become a well rounded IT security professional. Therefore, you probably wonder why I spend so much time talking about identity management software over other security technologies. As hard as I try to stress…
-
Improving Password Security Shouldn’t Be Rocket Science
Password security blueprint. It amazes me that, despite all the money being spent on security measures, from endpoints to data leak prevention to database security, the single largest vulnerability continues to be passwords. To be specific, 76% of all breaches over the past few years were based on weak or stolen password credentials according to…
-

This Year’s Gartner Symposium ITxpo Had Risk Written All Over It
Gartner Symposium Booth 547. As the 2014 Gartner Symposium ITxpo draws to a close, I must admit it was one of the most stimulating, thought provoking symposiums I’ve seen. As advertised, the sold out show brought together over 8500 participants with 3000 CIOs to hear outstanding speakers from throughout the industry. What struck me, however,…
-

Take Leadership ACTION When Undertaking an IT Risk Assessment
IT risk assessment influence. No matter how mature an organization is with managing security, it is almost guaranteed that some facet of security can be improved or overhauled at any given time. So where do you begin? This is why performing IT risk assessments is a critical component of any security program. Everyone agrees that…
-

“Do You Feel Safer?” 911 from an Information Security Perspective
Information security 911 preparedness. Thirteen years after one of the most horrific terrorist attacks on America, I have to ask myself "do I feel any safer?" Like you, I’m sure, the answer is "no." On the other hand, the risk I feel now has less to do with a physical attack and more to do…
-

For the Gartner ITxpo, Does the Early Bird Really Get the Worm?
Check out Avatier at the Gartner ITxpo to capitalize on innovation. I never do today what I can put off until tomorrow. My wife is just the opposite. With the Gartner ITxpo already just a month away, she suggested I provide a preview of what looks good. Today, in late August. Clearly, you can see…
-

The True Value of an Information Security Compliance Auditor
Information security audits add up. I recently read the KPMG Value of Audit, The Audit Model and the Profession by Rupert Bruce. Although the focus was on financial audits, the journal resonated with me as an information security auditor. Several takeaways made the article worth review. Beginning with the assumption ‘auditor’ is synonymous with ‘compliance…
-

Information Security and IT Leadership Business Accountability
IT leadership get aligned. In my last article, I discussed the need for IT leadership to start transitioning accountability to the business, but I primarily focused on security-related aspects of this transition. In this article, I highlight broader IT-related culture and process changes that can help organizations begin to deliver greater capabilities by engaging with…
-

Think Broader than the “A” in IAM Identity and Access Management
Identity and Access Management (IAM) applies to more than just accounts. From working with various organizations, it is interesting to listen to differing perspectives about what capabilities identity and access management should encompass. Some people continue to believe that identity management only applies to accounts and access. This thinking limits operational and security improvements and…
-
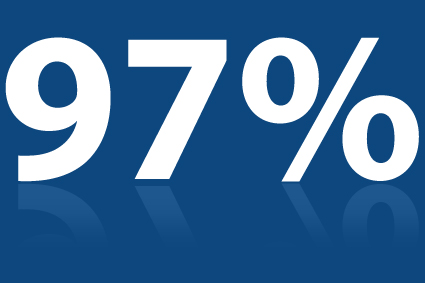
97% Customer Renewals for Avatier Identity Management System
Customer Renewal Rate. Recently, I was fortunate to work on the Why Avatier web page. My role was small in terms of the content I contributed. Yet, the impact reveals our company’s heart and soul. It’s the drive behind what we call business focused user-centric innovation. Before I started, I knew we had wildly successful…
-

Avatier Spins Off IT Security Consulting Company
At last, fixed-price IT security services. Last week we announced the launch of the IT Security Consulting Company, a spinoff of Avatier. We are using the expertise of this new group of consultants to provide services in all areas of information security including Identity and Access Management. Initially, we will be concentrating on sixteen areas:…
-
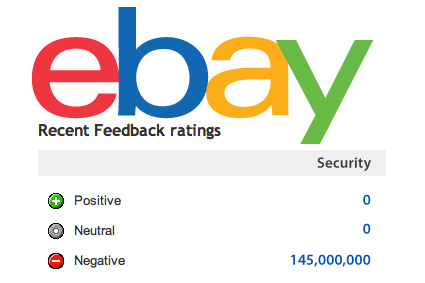
EBay Privileged Account Management Auction
eBay privileged account management feedback. I must confess. I am a little surprised by the media’s response and coverage of the eBay information security breach where hackers gained access to the personal data of 145 million customers over a four month period. During this time, cyber criminals accessed a database containing customer names, their email…
-

The Culture of Cloud in an Information Security World
Cloud information security cultural transformation. Working in the information security field, I obviously hear a lot about “the cloud” and its many security implications. There are definitely valid security concerns associated with cloud computing, but isn’t the entire industry of “information security” based on the concept of “securing information” no matter where it resides (including…
-

EDUCAUSE Security Professionals: Meet Me in St. Louis, Louie
At the EDUCAUSE Security Conference, the force is strong. The 12th Annual EDUCAUSE Security Professionals Conference 2014, drew from two audiences this week in St. Louis. Over 400 security staff, IT staff, privacy officers, and others from the higher education community with an interest in security and privacy were there in force—and a multitude of…
-

Avatier Packs Major Identity Management Changes into AIMS 9.5
Liftoff! This month the company launched the latest version of its Avatier Identity Anywhere (AIMS) providing several significant additions. AIMS 9.5 now includes SMS self-service password reset, a new patented approach to increased IT store intelligence, and revolutionary risk mitigation throughout. Enterprise Password Management AIMS’ Password Management module now features SMS two-factor authentication without requiring…
-

2014 RSA Conference Three Big Easy Wins
Security engagement. Some equate the annual RSA Conference to the Lollapalooza of information security events. I don’t always agree with this premise. However, this year’s conference was exceptional. Perhaps it’s San Francisco or maybe the times we live in. This 2014 RSA Conference did not disappoint. It delivered a full week of pomp, regalia and…
-

The Four IT Security Principles: A Practical Guide to Improving Information Security
Security Commandments. Below are four principles to help you become a more effective IT security leader. While these principles won’t solve all your problems, if you practice them regularly, you can’t help but reduce risks and knock annoying security problems off your to-do lists. Start a difficult information security task Every IT security leader has…
-

How an Identity Manager Stops Edward Snowden Administrators
Privileged whistleblower. Since Edward Snowden’s release of over 1.7 million classified NSA documents, trusted identities and privileges require re-examination. While opinions regarding Snowden range from traitor to Noble Prize winner, his actions delivered a wake up call to IT leaders. As an IT security professional, whether you support or abhor Snowden’s actions, you must take…
-

Have A Hacker Over For The Holidays
Cyber Carol ‘Twas the night before Christmas and all through the house, many creatures were stirring while holding a mouse. Their stockings were hung by computers with care, in hopes that their breakins soon would be there. It turns out you don’t really need to invite a hacker over for the Holidays… they’ve invited themselves.…
-

THE VIRTUAL VOYEUR
Attendance recommended. Participation a must. I’m not there and I should be. Time is money and I don’t have enough of either. So what’s the answer? One of the nation’s top conferences has figured that out. EDUCAUSE, the premier IT conference for the education industry, is in full swing this week with over 400 educational sessions…
-

Better Enterprise Risk Management: Keep Your Priorities Straight with Balanced Scorecard Software
Balanced scorecard alignment. If you’re in charge of information security risk management for your organization, you know that the process is a study in trade-offs. You have to deal with acute, urgent problems — happenstances that are disrupting workflow in the here-and-now. But then there are those chronic drags — costly inefficiencies, latent security vulnerabilities…
-

Stopping the ‘Enemy Within’ with IT Risk Management Software
Self-service IT risk management. If ever organizations questioned the need for IT Risk Management Software, one simple statistic about cyber security cited recently in the National Law Review should change their minds: “According to Diligence Information Security, about 70 percent of security breaches are committed by employees.” Yes, those dedicated individuals who depend upon your…
-

Think about "Risk Management" when Outsourcing Information Security
Outsourcing information security risks. I have never been a huge fan of outsourcing information security, especially when security operations and vulnerability management are intermingled with infrastructure outsourcing deals. I have had first-hand experience at previous companies dealing with the risks of all aspects of outsourcing from selecting ITO providers, migrating from one provider to another…
-

Cyber Security: How to Cover Your SaaS
Reach for SaaS cyber security. While attending various conferences, roundtables and other information security gatherings, a common theme that often presents itself is the concern over security of software-as-a-service (SaaS) vendors. Another common theme seems to be that IT cyber security teams are either very confident with how they are managing this particular “cloud” risk…
-

Solid Cyber Security Takeaways from ISSA Chapter
ISSA IT security experts gather. I recently attended my local ISSA chapter meeting, and there were some key takeaways relating to successful cyber security management practices amongst the group. In order to enlighten blog readers, I thought I would highlight some of the successful practices to hopefully inspire others out there to up their game.…
-

Top 10 Cyber Security Software Hacks on Santa’s 2012 Most Naughty List
Top holiday cyber security hacks. Here we are, one year older and one year wiser when it comes to cyber security software, but unfortunately it seems those who mean to undermine cyber security systems have also grown. While there seemed to be a lot more high profile attacks on government and private business in 2011,…
-

How to (Quickly) Close the Door on Cyber Security Threats
Cyber security threats shut out. In today’s age of IT cyber security threats, there are always new risks that need to be monitored and accounted for, but all of the old threats still need to be top of mind as well. Information security is a function where new responsibilities continue to grow and where old…
-

Gartner Identity and Access Management Summit Wraps Up
Gartner Identity and Access Management insights. It was quite a week in Las Vegas for the annual Gartner Identity and Access Management (IAM) Summit. While Avatier may not have been exactly a household name going into the conference, we certainly did our part to spread the message about the innovative ways the company is taking…
-

A Corporate Cyber Security Risks Wish List
IT security greeting. God rest ye merry IT men, let nothing you dismay; Remember hackers’ prime season began on Black Fri-day… While Avatier shows off its new access certification tool, Compliance Auditor, at the annual Gartner Identity and Access Management (IAM) Summit next week, a special group of people around the world is busy preparing…
-

After Turkey Day Avatier Goes for "All the Fixin’s" at Gartner Identity Management Summit
Gartner IAM Las Vegas. This week, hearts and minds across the U.S. are focused on the upcoming Thanksgiving holiday and all that it offers — giving thanks, being with family and eating lots and lots of turkey with all the fixin’s. While we at Avatier join others in these thoughts, in the backs of our…
-

Top 5 Cyber Security Access Certification Measures to Rock the Online Vote
Access certification and the future of voting. Last week our country voted to keep a president and change our congress… and not a single shot was fired in anger to do it. I’ve been enthralled by the seamlessness of this process since a very young age. By 9 years old, I was already pouring over…
-

CIOs Heads Not in the Cyber Security Cloud
Cloud computing cyber blues. BREAKING NEWS: THE PRESTIGIOUS CONSULTING FIRM, ERNST & YOUNG, RECENTLY REPORTED IN ITS 2012 GLOBAL INFORMATION SECURITY SURVEY THAT CIOS ARE LEERY ABOUT THE SECURITY OF CLOUD COMPUTING SYSTEMS. IN OTHER NEWS, WATER IS WET, THE SKY IS BLUE AND SIBLINGS FIGHT. Trepidation over cyber security cloud computing issues is not…
-

Cyber Security Threats: Is World War III Upon Us?
Eminent cyber security threats. Albert Einstein once said, "I know not with what weapons World War III will be fought, but World War IV will be fought with sticks and stones." Ever a man ahead of his time, were he alive today it’s likely the only thing he would change about his statement would be…
-

KuppingerCole ‘Compass’ Points to Identity Management Software Innovator
KuppingerCole recognizes innovation. Innovation is one of Avatier’s core values and a key to its cyber security strategy in identity management software. But it’s one thing to tell people you’re innovative; it’s another thing all together to have an expert in the identity management software field confirm it. That’s what happened last week when KuppingerCole,…
-

5 Steps for implementing a BYOD identity governance solution
BYOD access provisioning. I began writing about technology systems at the dawn of the handheld era. The first time I ever wrote about the use of a mobile device in the workplace was in regard to an unwieldy piece of hardware with a monochromatic screen used by nurses for bedside documentation of patients’ vital signs…
-

Identity and Access Management (IAM) Integration Reaches for the Cloud
IAM in the cloud. I confess that I’ve been around the Tech industry long enough (i.e., the 1990’s) to recall when "working from home" was not an easy thing to do. For most companies back then, when an employee wanted to work from home he or she usually did not have a way to connect…
-

Reviewer Calls Avatier’s Identity and Access Management Software Suite ‘A Remarkable Offering’
Best identity manager. SC Magazine, one of the most highly regarded publications covering the IT cyber security space, recently published a review of Avatier’s Identity and Access Management (AIMS) Software Suite. The suite, which is Avatier’s main identity and access management software product and incorporates products for user provisioning, password management, governance risk compliance, and…
-

There is No "One Size Fits All" Solution to Cyber Security Incident Response
Cyber security incident response on shaky ground. When speaking of “an ounce of prevention” is worth more than “a pound of cure” it is unlikely that you will find many who disagree with the sentiment and the IT world seems to have taken this concept as its personal mantra. New technologies and system updates are…
-

Bring Your Own Identity and Access Governance?
A manager’s identity and access governance duties. I think that a lot of people out there are familiar with the concept of BYOD or "Bring Your Own Device", even if they don’t consciously realize it. I had never heard the term until very recently and realized that I had been using my personal smartphone at work…
-

Empowering Users Is More Than an IT Service Catalog Fad
An ‘actionable’ IT service catalog. It’s been fascinating over the years to watch the network architecture pendulum swing back and forth. First, networks were organized around a mainframe with what were then called dumb (now more respectfully referred to as thin) clients. Then we moved into the client/server era, where users revolted at the dictatorial manner…
-

How Can You Present Information Security Metrics Better?
‘Actionable’ information security metrics speak millions. Security professionals continue to struggle with collecting and presenting information security metrics in an effective manner. Attend any information security conference and you will find experts discussing the need for balanced scorecard reporting and the types of information to include in information security metrics reports. Unfortunately, even with all…
-

Cyber Security Solutions Begins with You
President Obama’s cyber call to action. In case you missed it, President Obama wrote an extraordinary editorial that appeared in last Friday’s Wall Street Journal, focusing on cyber security threats on America’s infrastructure. The article begins by describing a simulation of multiple cyber security threats focused on deploying malware on critical systems that operate transportation,…
-

Forget the Wide Net — Spear Phishing is the Next Big Cyber Security Threat
Cyber criminals spear phish. We’ve all been warned about cyber security phishing, and many of us have received emails sent by cyber criminals that link back to phony branded websites requesting personal data. We’ve been told to be wary of suspicious “from” addresses, spelling errors and unfamiliar URLs, and subsequently we’ve become significantly savvier —…
-

Cyber Security Threats and Attacks Put Economy at Risk
Cyber threats costs us all. It should come as a surprise to no one who follows the news that cyber security threats are on the rise in the U.S. and that the security of every business not innovative enough to thwart cyber attacks is at serious risk. The fact that employees remain points of vulnerability…
-

It’s Criminal to Overlook Access Management Software
Prevent white collar crime. So much crime today occurs because nobody is paying attention to the identity and access management software. I was reminded of this last week when the National Credit Union Administration — the federal agency that oversees credit unions — barred Edgar Kelly from having dealings with any federally insured financial institution.…