Category: IT Risk Management
-

Password Hygiene in Banking: Best Practices for Security Teams Using Avatier’s Assistant
Discover the best practices for password hygiene in banking with Avatier’s innovative solutions. Learn how to enhance security.
-

How AI-Driven Access Certification Enhances Bank Security with Avatier
Explore how AI-driven access certification revolutionizes bank security with Avatier’s solutions empowering financial institutions
-

Should You Implement Passwordless Authentication?
Passwordless authentication is an emerging concept in IT security. It is a way to replace the shortcomings of traditional passwords while protecting IT security. As a newer technology, it might be helpful as a way to reach your security goals. Discover what exactly passwordless authentication can do for your security and identify the challenges with…
-

Covid and Identity Management
COVID-19 changed the business world forever. Back in March 2020, few of us imagined that the crisis would last more than six months. At this point, it is time to apply agile thinking to adjust identity and access management practices to respond to the current situation. Ways COVID-19 Has Changed The Identity and Access Management…
-

Blockchain IT Security: The Fundamentals You Need To Know
Blockchain security, the critical technology between new digital currencies like bitcoin, is becoming more significant. As an IT security leader, you may be asked about blockchain security and what it means for the future of technology. Use this article as a resource to understand the main ideas related to blockchain. Why Does Blockchain Technology Matter…
-

How To Define The Role of MFA In Your Remote Work Policy
There are a few ways to look at the meaning of MFA (multi-factor authentication). There is a simple technical definition of MFA, which we will cover next. That knowledge alone is not going to keep your company’s data safe. Instead, you need to develop your approach to MFA for your company’s situation. Specifically, you will…
-

What Does SSO Mean For Remote Education?
The answer to the question of what SSO means has a technical answer and a context question. You will find out the meaning of this important IT security term—SSO (also known as single sign-on)—and what it means for remote education. What Does SSO Mean: A Short, Technical Definition The specific technical details involved in single…
-
What Is Multi Factor Authentication?
If you’re asking what multi-factor authentication (MFA) is, you have come to the right place. You’re about to learn the definition of this IT security concept, but that’s not all. You will also learn how to bring this critical idea to life in your organization. What Is Multi-Factor Authentication: A Practical Definition The simplest way…
-

Build Your Remote Learning Security Business Case
Remote learning has exploded in popularity in 2020. CNBC reports that half of elementary and high school students in the United States will use remote learning this year. That’s millions of students, and it doesn’t include college students. Designing a remote learning program at this scale means that administrators need to be mindful of security…
-

How To Onboard Remote Employees Securely
Employee onboarding is a critical moment for your organization and the new hire. Get it right, and you will find that everyone achieves productivity quickly. Further, your new hire will be positioned for success, and you will make the most of their positive attitude. On the other hand, a failed or poorly coordinated employee onboarding…
-

The New Way To Reduce Fraud Losses Before They Happen
Fraud losses cost companies billions of dollars every year. According to the Nilson Report, payment card fraud losses reached $27.85 billion in 2018. That is just one type of fraud! There are multiple types of fraud, including internal fraud (i.e., caused by employees or those facilitated by employees) as well as traditional external fraud. There…
-

What You Need To Know About HIPAA Compliance Violations
HIPAA compliance violations are costly – fines over $25,000 still happen! Fortunately, you can learn from the mistakes of other organizations.
-

HIPAA Compliance reporting In 1 Hour Per Week
Does your HIPAA Compliance reporting take hours or days to implement? It doesn’t have to be that way. Use this step by step plan to produce your reports in one hour per week.
-

What IT Security Professional Need To Know About Deepfake Technology
The deepfake threat is real, and the Pentagon is working on stopping it! Find out how to analyze and defend against this emerging risk with our guide.
-

Why HIPAA compliance is becoming more challenging
Your traditional approach to solving HIPAA compliance is no longer good enough. When HIPAA regulations first became commonplace, there was a surge of compliance effort. Your organization may have hired trainers to guide your staff. You might have modified or installed new technology systems. For a time, these compliance measures kept you on the right…
-

Reduce Your Exposure To Microsoft Teams Security Vulnerabilities
Reducing Microsoft Teams security vulnerabilities should be on your priority list if your organization relies on this collaboration tool. In contrast to email and other established tools, Microsoft Teams is still relatively new. That means you need to evolve your IT security processes to manage security risk. There will be some growing pains as you…
-

Solving The IT Security Skills Gap Without Hiring
New IT security threats strike every day. Financially, the impact of IT security failures continues to grow. A White House report estimates that cybersecurity attacks cost the U.S. economy over $50 billion per year. To combat these threats, organizations need to have the right talent. The IT Security Skills Gap Challenge And What It Means…
-

Are You Using These Solutions To Cybersecurity Stress?
Cybersecurity stress is a real and growing problem for many companies. It just takes one glance at the news to see why. CNBC reports that many cybersecurity attacks cost more than $200,000 to address. As a result, a growing number of companies are going out of business when they suffer an attack. The traditional approach…
-

How To Reduce Microsoft Teams Data Security Risk
Improving Microsoft Teams data security isn’t difficult when you have a process. If you don’t follow a process, this application will continue to be a source of risk. It could be the loose end that causes all manner of chaos and security incidents. Use this three-step plan to keep your confidential data in Microsoft Teams…
-

HIPAA Compliance for Telehealth: The Key Security Tips You Need
HIPAA compliance for telehealth has rapidly become a central priority for health care providers. Eighty-one percent of Americans own a smartphone, according to the Pew Center. Further, more than 50% of Americans aged 65 and over own a smartphone. Since older people tend to need more health care resources and many of them now have…
-

Paycheck Protection Program Security: What You Need To Know
Business owners and employees going through tough times need help. That’s why programs like the Paycheck Protection Program exist. There’s just one problem. Whenever new programs are developed, some unethical people try to cheat the program. Specifically, some hackers may try to defeat your Paycheck Protection Program security. To keep your company safe, it is…
-

The Right Way and The Wrong Way To Optimize IT Security Costs
In many organizations, the IT security cost line item in budgets just keeps increasing year over year. Companies like Bank of America are spending over $500 million on IT security. IT managers need to be prepared to respond to executives if and when they ask for a reduction in IT security costs. However, there is…
-
HIPAA Compliance vs. iso 27001: Security Requirements You Need To Follow
When you build your IT security program, you don’t have to start with a blank page. Instead, you can leverage existing security standards. However, these standards have different requirements. To get you started, let’s take a closer look at two of the most popular IT security standards: HIPAA compliance vs. ISO 27001. HIPAA Compliance: The…
-

Work From Home Security: How To Train Your Employees Fast
Work-from-home security is getting a lot more attention because millions of employees are now working remotely. Unless you provide direction, your employees may accidentally act in a less secure manner. After all, working from home requires new behaviors, habits and processes to maintain organizational security. To make sure your work from home security training is…
-

Microsoft Teams Security Best Practices: 5 Tips You Can Use This Week
If you use Microsoft Teams, you need these Microsoft Teams security best practices. This collaboration technology product is excellent for engaging employees when they are remote or based in different locations. However, your IT security measures also need to keep pace so you do not suffer a breach. Your first move is to focus on…
-

How To Present IT Security Updates To Your Executives In 60 Minutes
Have you been asked to provide updates on IT security for executives? That’s a tough challenge for many IT security professionals and managers. You’re comfortable diving into the details — looking at threats, testing systems, and more. Boiling down everything you have to say for an executive audience requires a new perspective. You need to…
-

Meeting the US Government’s ICAM Requirements
ICAM (Identity, Credential and Access Management) is a key information security requirement for the US government. Whether you are in government or serve the government as a supplier, these requirements matter. You may already have an identity and access management program in place. However, that program may be fully aligned with ICAM expectations. Before you…
-

Speed Up Your Vulnerability Management Response Times This Month
Vulnerability management never stops and never slows down. If you miss a notice, you are leaving a door to your company’s systems unlocked. Like an incident response, vulnerability management requires that you act fast! Every day that goes by without action increases the chances of an incident. At the same time, it can be tough…
-

How To Boost IT Security Skills Across Your Company
The quality of your IT security skills may mean the difference between data loss and high security. Encouraging your team to develop better IT security skills on their own time is unlikely to be effective. Instead, you need to develop an enterprise strategy to identify critical skills and equip your staff to succeed. The Right…
-

Single Sign On Security Mistakes To Avoid In 2020
Single sign-on mistakes are quite common. IT professionals get excited about the technology since it makes life easier for employees. However, if you approach a single sign-on technology solely as a convenience tool, you will have problems. Specifically, you will increase your security risk! To keep your organization safe, make sure you avoid these mistakes.…
-

How To Automate IT Security In Your Supply Chain
IT security supply chain risks are increasing. Outsourcing, the increasing use of integrations between different software packages, and regulation are part of the story. Define Your IT Security Current State For Your Supply Chain If you make the wrong changes to your supply chain, you might make security worse. To avoid that situation, slow down…
-

Managers: How To Maintain Security With Your Newly Remote Workforce
Remote workforce management requires special skills. You can’t just “drop by” to see how your people are doing. You might wonder if your remote workforce is staying productive, especially if they are new to remote work arrangements. Optimizing productivity is worthwhile. However, all the productivity in the world can be wiped out by an IT…
-

Six Ways Manual IT Security Practices Increase Security Risk
Manual IT security is quietly making your organization more vulnerable to security incidents. If you keep relying on manual processes, protecting your organization will become much more difficult over time. You might not be convinced yet. To prove it to you, here are six ways that manual IT security practices and processes cause security problems.…
-

Working From Home Security: Managing Multiple Users Securely
Work-from-home security requires a new perspective and new technologies. You still need to meet your security objectives, regardless of the environment. However, there’s a need to change your approach. Before making changes, start with an IT security risk assessment. This will ensure you find security issues that impact multiple users rather than responding to one-off…
-

Are Chat Services Helping or Hurting Your IT Security?
Chat services security is a hot topic today because these services have become so popular. For example, Slack has over 12 million active users. In terms of website chat services, Intercom alone is active on more than 76,000 websites. These chat services make it easy to ask a question and get an answer. However, that…
-

The 7 Habits of A Successful Work From Home Professional
Worried about the state of your work-from-home habits? Working from home, especially for long periods, requires some changes. If you haven’t found your groove yet, don’t worry. Use these work-from-home habits to improve your focus and stay on task. 1) Set Daily and Weekly Goals When you first start working from home, it can disrupt…
-
What You Need To Know About VPN Security
VPN security technology has become much more prevalent in 2020. It is one of the most popular ways to provide security for a remote workforce. Virtual Private Network (VPN) usage in the US grew 50% in March 2020, according to Network World. As you look at ways to scale up VPN to protect your organization,…
-

Working From Home: 5 Security Mistakes To Avoid
Work from home security has become a top priority for IT managers and professionals across the world this year. If your company is used to having most staff in the office, adjusting to significant scale work from home takes some adjustments. Fortunately, there are a few simple steps you can take to mitigate this risk.…
-

How To Self Assess Your PIPEDA Compliance
Protecting private information matters regardless of where you do business. However, each jurisdiction has different rules. If you want to do business in Canada, you need to follow the Personal Information Protection and Electronic Documents Act (PIPEDA). Before you find out how to self-assess your organization’s performance, let’s make clear why this matters. This law…
-

How To Use Rule-Based IT Security
How and when should you use rule-based security to protect your company? Use it effectively, and you will have more free time to focus on high-value strategic tasks. It’s a way to reduce employee burnout on the IT security team. You get to achieve more security protection with less manual work. That’s why rule-based security…
-

How To Present CCPA Compliance To Your Executives
You need to achieve CCPA (California Consumer Privacy Act) compliance. There’s just one problem. It is going to take resources and participation from multiple departments. Persuading people one at a time is not going to cut it. You need to win executive support for CCPA compliance. To win that support and keep your company out…
-

Avatier vs IBM Authentication Solutions
You’re looking at Avatier vs. IBM Authentication Solutions for your company. How do you make a smart choice? It’s true that IBM has an excellent reputation and many years in the technology business. However, it pays to take a more critical approach in evaluating Avatier and IBM’s approach to identity and access management. 1) Avatier…
-

When Should You Implement IT Security Automation?
You walk into your office and open your IT security to-do list for the day. If you’re like most of our customers, you will see dozens of tasks staring back at you. Yikes! Hopefully, you manage to make some progress on this mountain of work each day. Yet you wonder if there is a better…
-

The Most Overlooked Areas In IT Security Maintenance
IT security success requires constant vigilance. Last year’s processes and tools may no longer be good enough for today. For a security incident to happen, you need one weak link in your IT security chain. To lower the chances of an IT security incident, review these seven neglected areas of IT security maintenance. 1) Asset…
-

The Simple Weekly IT Security Maintenance Habit You Need To Stay Secure
There is a force that is quietly weakening your IT security week after week. Ignore this force, and your organization will suffer. No, we’re not referring to the “dark side” of the Force from Star Wars. Instead, we mean entropy – the tendency of systems to decay over time. You see it in the natural…
-
Evaluate The Effectiveness of IT Security Training In 5 Steps
Every year, you offer an IT security training program to your employees. You hope it is good enough to keep the company safe from phishing, spear-phishing and social engineering. There’s just one problem. If you have no way to verify the effectiveness of your training, your training might be creating more problems than it solves.…
-

Avatier vs Centrify
Identity and access management (IAM) is your first line of digital defense. The collection of technologies is your gatekeeper. It verifies a user’s identity, opening the door to your company’s files and software. Simultaneously, it denies access to unauthorized parties or users who don’t have the appropriate clearance. This may seem straightforward, but securing access…
-

Why Consumer Password Apps Increase Security Risk For Companies
Your employees are already using password apps at home and on their phones. You probably use them yourself. It’s convenient when your web browser saves passwords. Yet it is worth taking a step back and considering whether these convenience-oriented password apps are fit for purpose. What Is The Goal of Consumer Password Apps? When you…
-

3 Techniques To Introduce IT Security Automation This Year
Do you ever feel overworked in IT security? Do you find yourself dreaming of introducing IT automation? When we speak with our customers, we continuously hear about their tremendous workloads. In the morning, they have IT project meetings to attend. After that, there is email. You face even more work. There are new SaaS applications…
-

How To Improve IT Security Productivity With Narrow band AI Chatbots
AI chatbots are a popular business tool for sales and marketing. You’ve already seen those pop-up windows on websites offering to help you place an order or get an answer to a customer service question. This type of specialized AI is an excellent way to boost productivity in sales, marketing and customer service. Today, AI…
-

Improve Healthcare IT Security Without Hiring More IT Staff
Your health care information is some of the most sensitive data that exists. It tells the story of a person’s health, injuries and much more. If that data is exposed, you might face all kinds of painful consequences. That’s why healthcare cybersecurity is so critical. There’s just one problem: healthcare IT departments are overstretched, and…
-

5 Simple Steps To Keep College Students and Professors Safe From Attack
College IT security managers face a special challenge. Unlike companies, they have to manage thousands of new users every year. That means it is challenging to promote effective security habits. That’s not all. In college cybersecurity, you are also expected to protect sensitive records such as student records, research data and financial files. What Is…
-

Are You Using Enough IT Security Automation?
IT security automation is no longer a pipe dream reserved for companies with deep pockets. It’s a reality you need to embrace if you are going to keep up with today’s threats. Alas, your enthusiasm for this innovative technology may not be enough to bring your company on board. To help you make a case…
-

How To Protect Critical Energy Infrastructure From Cyber Attack In 5 Steps
How do you deliver critical infrastructure security in 2019 and beyond? There are no easy answers to that challenge because these are complex systems. Further, these systems are subject to complicated threats like hacking, natural disasters, internal threats and beyond. Don’t let the magnitude of the problem discourage you. The best way to approach critical…
-
How To Safely Use IT Security Automation Without Increasing Risk
Risk management is a guiding principle in IT security. To a degree, this caution and conservative attitude is helpful. It acts as a speed bump against reckless behavior. However, risk management should not prevent you from adopting critical innovation in IT security automation. We’ll guide through the process so you can improve productivity and manage…
-

Improving IT Security Audit Quality With Technology
What happens when you cut corners on audit quality? At first glance, it seems like an excellent way to save money. After all, audits don’t bring in new customers. Audits don’t improve your product either. However, rushing through a cybersecurity audit is short sighted. Let’s break it down and show you a better way to…
-

How To Save Time On Cybersecurity Audits In 5 Steps
Cybersecurity audit time! Nobody looks forward to cyber audits. Like going to the dentist, these audits are crucial to keeping your organization in good health. However, you can take steps to make the experience smoother and less time-consuming. To get you started on the right path, let’s first confirm why cybersecurity audits are so important.…
-

What You Can Learn From Password Failures In The News
Password news is a hot topic for IT security professionals and managers. When you think about the damage that a compromised password can do, this scrutiny is no surprise. There’s a problem with how most companies manage password news. They hear about these incidents in the news media or from colleagues at other organizations and…
-

Is Your School Vulnerable To Today’s Cyber Threats
As educators, you have a crucial responsibility to protect your students so that they can learn in a safe environment. Your school IT security practices are one part of the picture. Your physical security measures are another part. To prevent theft and misuse of your school’s IT assets and data, you need to apply a…
-

5 Ways To Use Narrow Band AI Chatbot
What can weak AI, also known as narrow band AI, do for your cybersecurity? The answer might surprise you. You might be inclined to be skeptical of artificial intelligence because you assume it requires a team of specialists. Fortunately, AI technology has come a long way, and it is now much easier to implement. To…
-

How To Self-Assess Your Health Care Cybersecurity
Health and money – you can’t go a day without thinking about these topics. That’s one reason why health care cybersecurity is such a hot topic. Imagine this: a patient comes into the hospital for a routine checkup. Then she finds out that she has an aggressive form of cancer. In a moment, her whole…
-

Meeting Energy Industry IT Security Requirements Step By Step
Winning at IT security for the energy industry is critical. With poor security in energy, the safety and health of people across the nation will be at risk. Hospitals will go dark. Traffic lights will malfunction. The economy will suffer, and people may lose jobs. All of this can be prevented by implementing better IT…
-

Are Your Cybersecurity Audits Comprehensive?
Cybersecurity audits are one of the best ways to get peace of mind on your IT security. Instead of waiting for hackers to break into the organization, you find problems and then fix them. Detecting cybersecurity problems through an audit and later correcting them is much less stressful than scrambling to fix problems after a…
-

Narrow band AI Chatbot
When was the last time you looked at chatbots? Your first impressions may have been disappointing. Maybe you heard about the famous Microsoft chatbot failure in 2016. The first generation of “narrow band” AI services certainly had problems. However, the industry is changing. Today, you can have access to already-trained and finely tuned chatbots to…
-

How to Use FIDO2 to Protect Remote Employees from Cyber Threats
In cybersecurity, there’s no such thing as “done.” You need to be on the lookout for new threats and opportunities. In the past, you tightened physical security and created a password policy. Now, you need to tackle the challenge of remote employee security. The Remote Employee Security Challenge Is Growing Years ago, you could prevent…
-
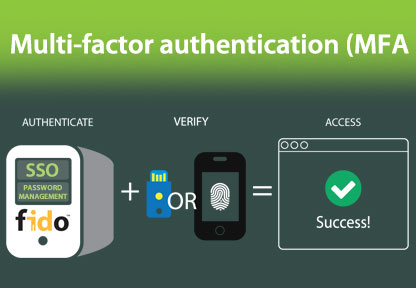
Here’s How Implement Multi Factor Authentication Faster with FIDO2
You want fast multi-factor authentication, but IT tells you that’s impossible. We’ve heard that story too, and we have some good news. There’s a way to make multi-factor authentication happen quickly. When you have MFA in place, and employees are using it, your organization will become much more difficult to hack. To show how fast…
-

Lessons Learned from Access Governance Failures in the News
If you know where to look, access governance news is everywhere. With the right perspective, you can learn from these events and improve your organization’s defenses. If you neglect these steps, you’ll be left behind by your more focused competitors who take every effort to improve security. Don’t let that happen to you; study these…
-

Executives: What You Need to Know About FIDO2 to Improve Security
As an executive, you have to make tough choices. Do you fund more training for your staff this year? Should you say yes to a proposal to have a consultant review your IT security? Each option has a benefit to offer the organization. When your managers ask you to approve FIDO2 cybersecurity, you need some…
-

The Simple Way to Pass SOX 302 and SOX 304 Reviews Faster
Keeping up with compliance requirements as a public company is a tough job. If you make one mistake with a SOX requirement, your company can face serious consequences. Before we look at ways to address these requirements, let’s take a step back and define a few key terms and concepts. Defining Key SOX Terms SOX:…
-

Cut Your IT Audit Time In Half
IT audits are essential to maintaining security and protecting information. By thoroughly evaluating controls and practices, IT audits help managers and employees to find problems and fix them. There’s just one problem with IT audits. They can be time-consuming affairs that take you away from your primary work, and that’s not all. If you receive…
-

Are Your Contractors Increasing Your Cybersecurity Risk?
The rise of outsourcing to contractors and third parties has delivered great benefits. Your organization gets more flexibility and access to great expertise. However, this model does have some significant drawbacks. It’s more challenging to maintain IT security. IT contractors may have multiple clients, so they don’t have the same day-to-day focus on your organization.…
-

5 Steps to Make Cybersecurity Easy for Your Managers
How do you feel about the phrase “easy cybersecurity?” If you’re like most security professionals, the phrase probably makes you feel nervous. You might feel that “easy” means sloppy and inconsistent. There’s a different way to look at it. When you adopt easy cybersecurity for end-users, you end up protecting the organization more effectively. Why…
-

How to Identify and Protect All Corporate Assets (Not Just Computers and Mobile Devices)
Knowing is half the battle. That’s one piece of wisdom we learned from GI Joe. In the world of IT security, it applies throughout your program. The IT security program you developed a few years ago is probably out of date. What about Internet of Things security? Your current approach may be missing coverage for…
-

Is Your Cybersecurity Delivering Value For Money
There’s an awkward question that nobody wants to answer in the cybersecurity profession. If you avoid this question, non-security professionals will answer it for you. You owe it to the organization to face this question directly and give a thoughtful answer. The question is simple: What cybersecurity cost should your organization pay? However, the answer…
-

Why Implementing MFA Helps You Sell To The Enterprise
Multi-factor authentication (MFA) implementation is a way to improve your security resiliency. Most know that. However, did you know that it could also help your company win more enterprise customers? If you’ve ever wanted to demonstrate alignment with the business, this is one of your business opportunities. What Does MFA Implementation Tell Your Clients? To…
-
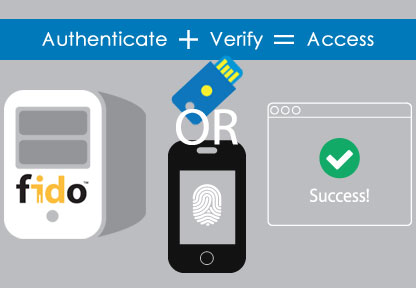
Make Multi-Factor Authentication Easy for Your Employees with FIDO2 Support
Improving security is a tough sell to employees. You need to convince them to change their habits. You have to monitor them to see if they’re following the new security protocols correctly. Think about increased security from the perspective of your end-users. They have a job to do and just want to get it done.…
-

The Top 7 Most Common Cybersecurity Mistakes Made with AI
Your company has started to use Artificial intelligence (AI), but are you effectively managing the risks involved? It’s a new growth channel with the potential to boost productivity and improve customer service. However, particular management risks need to be assessed in cybersecurity. Start by considering AI trends to put this risk in context. Why Is…
-
How to Update Your IT Security Policy With Multi Factor Authentication
What is the single document you need to organize all your IT security activities and practices? It’s the IT security policy. This document sets out the roles and responsibilities of everybody in the organization. You can also use the IT security policy to provide guidance on when to use certain types of security technology, such…
-

How to Protect Executives with MFA Security
As corporate leaders, your executives are highly visible representatives of the organization. The public knows the names of your executives and what roles they play. Likewise, hackers know the same information. Instead of taking the long path of breaking into multiple systems, a focused attacker merely needs to impersonate one of your executives to cause…
-

How To Reduce Your SaaS Expenses With SSO
Unlike traditional on-premise software, SaaS software looks simple and cheap at first glance. That line of thinking is true to an extent. However, there’s a dark side to the fact that it’s easy to buy software as a service: you can buy too much and waste money. Fortunately, you can use SSO software to get…
-
How to Reduce IT Security Vulnerabilities with SSO
There’s no end to IT security vulnerabilities. You solve one problem today, and another will appear tomorrow. Is that just the nature of work in IT security? The way you answer that question will shape how well you protect your organization. IT Security Vulnerabilities: Reactive vs. Proactive Approaches In reality, you need to think about…
-

Biometric Risks You Need To Know About Before Using MFA
You’ve probably already seen people use facial recognition to log in with their iPhone. That trend tells us that introducing biometric or MFA authentication will probably not come as a shock in the workplace. However, you need to understand and manage implementation risks before you use this authentication method. Putting Biometric Authentication Risk in Context…
-
How to Reduce Phishing Problems with SSO
Picture this: You receive an email from the Vice President of your department. She asks you to approve a payment on a website. Since the email appears legitimate, you click through to the website. After further review, you decide it’s a scam. Unfortunately, you’ve only partially protected yourself from a phishing attack. By opening the…
-

The Simple Way to Reduce Your IT Security Audit Findings
Few managers look forward to their annual IT security audit. It’s a painful experience for everybody involved. You have that sinking feeling of an outsider looking over your shoulder quietly listing mistakes. Some auditors see themselves as quasi-police investigators determined to find evidence of wrongdoing! While that approach leads to robust audits, it makes managers…
-
How to Leverage Slack and Skype to Save Time in IT Security
Ask 10 IT security professionals about IT security productivity; you’ll quickly find yourself in a heated debate. Cautious professionals will want to restrict using newer tools and apps because they introduce uncertainty. Other IT security leaders favor innovation and ask, “how can we make these tools work?” rather than aiming to shoot them down. If…
-

The Reason Why Employees Hate the IT Security Department
When everything goes right in IT security, nothing happens. No systems fail. There are no headlines in the news media. Nobody calls you at 3am about a crisis. It feels like you have no cybersecurity challenges. That’s one of the most frustrating realities of IT security work. On the other hand, many employees complain constantly…
-

Four Ways Cognitive Bias Hurts Your Cybersecurity And How To Address It
Your employees can make or break the success of your cybersecurity program. Social engineering attacks, carelessness, and mistakes are constant challenges. When you’re an IT security professional, you’re constantly thinking about risk exposure and the best ways to defend the company. Other employees have different concerns, such as shipping orders, making sales, and managing staff.…
-

The Path to Faster IT Security, No Expensive Change Management Required
Every month, there are new information security problems. Your servers are hacked, and you set up an incident team to recover from the issue. Next, your developers want to implement machine learning, and you worry about security exposures. No matter how hard you work, there are always new IT security threats. Why You Always Feel…
-

How to Improve Cybersecurity Agility Without Cutting Corners
You developed a cybersecurity framework to identify threats, educate users, and protect your most important assets. On paper, your organization looks well protected. In reality, you know the truth. Several parts of your cybersecurity framework aren’t implemented fully. If this situation sounds familiar, read on. Cybersecurity Framework: Plans vs. Reality Your cybersecurity framework was probably…
-

People Managers: How Chatbots Cut Down Your Admin Work
Your people managers spend too time much on administrative tasks. Every hour, they waste energy and resources that could be better spent on growing the business. Ignore this reality, and you’re going to fall behind your competitors. The High Cost of Managers Working on Administrative Tasks Will Surprise You Some amount of paperwork is inevitable…
-

How to Cut Wait Times to Resolve Complicated IT Security User Requests
The longer business users wait for a response to an IT support request, the less happy they’ll be. Years ago, you could get away with telling users to wait for hours or even days for a response. That’s not going to cut it anymore. The rise of same-day delivery from Amazon and instant service from…
-

Improve IT’s Reputation In Your Company By Cutting 99% Of Support Errors
There’s a specter haunting IT support departments across the world. It’s quiet. It’s invisible. This phenomenon causes other executives to ignore the CIO. It’s the scourge of a bad IT reputation. If the IT support department continues to have a low reputation within the organization, it’s only a question of time before the CIO is…
-

What Is the Cost of Implementing AI Today?
You’ve surely heard exciting news about artificial intelligence (AI), but is it right for your company? After all, you’re seeing headlines about investors pouring funds into AI: SAS is investing $1 billion in AI in 2019. Fortunately, there’s some good news. The cost of implementing AI in the enterprise is steadily falling. Before you start…
-

Should You Use AI in Your IT Security Operations?
Artificial intelligence (AI) tools require a PhD and a huge budget! If that’s what you’re thinking, pay attention. In the past few years, AI tools have dropped tremendously in price. These tools are also more user-friendly than ever. Instead of dedicating years of R&D effort to AI, you can buy AI services off the shelf.…
-

Can You Stretch Your IT Security Budget 30% Further with This Technology?
According to job search engine Indeed, the average salary for IT Security Specialists in the United States is now over $115,000. Build a small team of IT security specialists and you’ll easily spend millions just to keep pace with the market. Increasing IT salaries is just one challenge IT leaders face. They also have increasing…
-

The Must-Have IT Security Maintenance KPIs
You need to measure success in IT security. If you don’t, your requests for tools, resources, and budgets are going to be ignored. That’s not the only reason; measuring IT security through KPIs helps you perform better as a manager. You can recognize staff excellence by pointing to their performance and help them advance in…
-

5 Steps to Get Virtual Agent Technology Approved and Funded This Month
Virtual agents are the next leap forward in delivering increased productivity. However, it remains a new technology, so gaining approval for virtual agent technology will require some preparation. You’ll have to make a pitch that proves this technology is a better investment than other options. Use this five-part checklist to raise your odds of success.…
-

The Hidden Reasons Why Containers Help HIPAA Compliance
Just imagine if your health records leaked into the public domain. That might include your prescription data, photos, and medical test results. That’s what a HIPAA compliance failure looks like for the public. For hospitals and other health care organizations, there’s also a world of pain. You have to answer uncomfortable questions from the news…
-

The New Way to Provide 24/7 IT Support to Employees Without Working all Night
Employees want a seamless experience at work. There’s less and less patience for slow systems and bureaucratic delays. For IT leaders, this new expectation for an improved employee experience presents a new challenge. Traditionally, corporate systems prized control and scale over ease. If you want to be seen as a leader aligned with the business,…