Category: Identity Management
-

How IAM Makes ITSM Better—And Why They Belong Together
Add self-service IAM to your ITSM ticketing system. The goal of the IT organization is to create and protect business value. The "create" element seems widely understood; the IT service management function demonstrates value through the support and delivery of high-quality, cost-effective services that enable the business to meet their goals and objectives. The better…
-

Charlie Sheen A HIPAA HITECH Tragedy
Identity management automation peace of mind. I actually feel sorry for Charlie Sheen. I’m sure Charlie has his character flaws along with excessive fame. I am also certain he is entitled to his medical privacy. When you consider, people in his private circle blackmailed him. Most would agree he is a living tragedy. For all…
-

Time to Expire Phishing Strikes and Security Breaches
Detect cyber attacks before they score. In studying timelines of enterprise security breaches, organizations must shift their focus. Rather than firewalls and perimeter defense, the real damage occurs once inside. The longer cyber thieves remain unexposed the greater the cost. The 2015 Verizon Breach Report indicates 45% of attacks are initiated by phishing. As a…
-
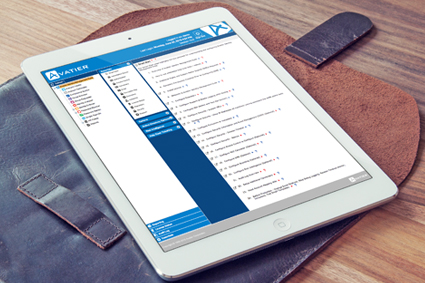
Contextual Learning an Identity and Access Management Configuration Differentiator
Contextual learning accelerates the value you receive from an identity manager. To lower costs, businesses seek configurable solutions over custom developed IT applications. Most IT organizations do their best to avoid customizing enterprise apps. Customizations tend to be costly while creating maintenance challenges. As a response, identity management vendors are providing greater configuration options. Areas…
-

Gartner ITxpo Showcases Identity Management Prevention Controls
Identity management takes center stage at this year’s Gartner ITxpo. The Gartner Symposium ITxpo tends to be broad and scattered with numerous IT security and risk management solutions. Generally, at the Gartner ITxpo, participants do not naturally see the connection between identity management and information security. At this year’s 2015 ITxpo, the roadmap to security…
-

New Identity Management for the Mobile Workforce Avatier Identity Anywhere (AIMS) 10
Identity management just got mobile. As the global leader and innovator of the most user-centric identity management software on the market, we are proud to announce at the Gartner ITxpo 2015 the release of the Avatier Identity Anywhere (AIMS) 10. As the newest and most powerful upgrade to our solutions used by millions of users…
-

Four Stages of Identity Management User Provisioning Automation
Take on user provisioning automation. We often tend to want it all and we want it now. Lost in this mindset is time and activities required to reach fruition. Similarly, I see this with identity management. Customers seeking vendors in the earlier stages want it all. They also assume they should have it all on…
-

KuppingerCole Digital Risk and Security Awareness Survey Paradox
KuppingerCole is a leading identity focused information security analyst company. After reviewing KuppingerCole’s, Digital Risk and Security Awareness Survey, I have a goal. In joining my associates with improved cyber security awareness, I must confess. I am not in the report’s minority, where I should be. As expected, most IT professionals see risks and threats…
-

MLB Steps Up to Identity Management Big League
Major League Baseball ushers in a new era of cheating. Baseball, known as America’s Pastime, reflects our national identity, culture and values. The 1967 Major League Baseball (MLB) World Series featured the St. Louis Cardinals. The Series remains one of my earliest memories. On a tree swing in the backyard, I listened to the game.…
-

Avatier Identity Management and Cherwell Software Strategic Alliance Makes ITSM and Enterprise Cloud Computing Better
Avatier announces a Strategic Alliance Partnership with Cherwell Software. Today, at the Cherwell Global Conference, we announced an incredible partnership with Cherwell Software™, a leading IT Service Management (ITSM) vendor, business and workforce enablement system. Our strategic alliance partnership with Cherwell ensures best practices are utilized in the design and implementation of the integration of…
-

Supporting Technologically Challenged Identity Management Customers
Hone in on the right level of communication for customer success. As technology changes and rapidly advances, all of us in identity management support work with customers who find themselves challenged by new and updated technology. As you might expect, a great deal of upset customers contact tech support. Many would rather cling to existing…
-

Top Identity Management in the Cloud Enterprise Applications
Most frequently requested enterprise cloud apps Let’s all agree. Identity and access management is core to IT security. Administration of software access and an individual’s credentials embody fundamental IT operations. Today, user management requires governing access to cloud and enterprise applications alike. Experts project global SaaS revenue to top $106 billion next year. This number…
-

NSA Map Shows Chinese Government Cyber Attacks on U.S. Targets
Over 600 reported cyber attacks since 2010. In the movie, Tucker: The Man and His Dream, Jeff Bridges plays Preston Tucker. As an entrepreneur, Tucker failed in 1947 to change the automotive industry. As a visionary, he succeeded in advancing automobile design, manufacturing and safety. In one scene, Tucker delivers an impassioned speech to investors.…
-
Four Ways to Preserve Customer Loyalty During Call Volume Spikes
How you respond during stressful times makes a difference. Remember building sandcastles? Constructing the towers and driftwood drawbridges was a blast. That is, until the tide came in and unexpected wave swept the beach and water flooded the kingdom. Only having prepared a deep and expansive moat did the realm remain safe. For everyone else,…
-

3 Enterprise Password Management Best Practices to Ensure User Adoption
Self-service enterprise password management operations. An enterprise password management solution benefits an entire organization, from IT and Help Desk staff to end-users. Implementing self-service password management improves help desk efficiency, reduces costs, and enforces strong security. It offers a win-win for everyone assuming you maximize adoption. To ensure high usage, a self-service password management solution…
-

IT Support Shifts to Self-Service Employee Empowerment
IT support transparency Today’s enterprise IT support organizations and help desks are experiencing a shift in the way technologies are developed, deployed and consumed. As with identity management, all applications and systems are evolving faster than ever, with new cloud-based solutions emerging to replace on-premise software of generations past. User expectations aren’t far behind; a…
-
NERC CIP Version 5 Compliance: Internal Controls or Executive Blinders
NERC CIP Version 5 internal controls. A few significant events occurred this week related to NERC CIP compliance that should not go unnoticed. Yesterday on July 1st, Version 5 of the NERC Critical Infrastructure Protection (CIP) quietly went into effect. Version 5 encompasses the most comprehensive updates since the standards launched in 2008. For some…
-

Eight Identity Management Practices for Stopping State Sponsored Cyber Attacks on Washington
Identity management defends against state sponsored cyber attacks. Last week Leon Panetta spoke at the Gartner Security Summit. His topic related to preventing cyber attacks in 2020. The irony was not lost considering four days prior. The Department of Homeland Security (DHS) announced our government’s largest security breach. Initially, ABC News reported four million employee…
-

Speeding Up the Gartner Security Summit
Gartner Security Summit Keynote Leon Panetta The Gartner Security & Risk Management Summit 2015 in Washington DC was no snooze fest. Quite the contrary. It’s just I don’t usually plan for security threats five years in advance. I’m engaged today. With the event infogram, "By 2020, 25% of global enterprises will engage the services of…
-

Four Myths of Self-Service Password Reset User Adoption
Myths support false premises I can generally tell how a self-service password reset project will go. Particularly, the ones which will struggle to sustain high levels of user adoption. In many cases, the initial sign doesn’t appear until after a purchase. It’s when the team involved in the evaluation and selection process drops down to…
-

From Overhead to Profit Center: How Identity Management Customer Service Is Evolving
User empowerment through customer self-service options. Embedded wiki content and training videos along with effective customer self-service are critical elements to developing a positive, powerful customer experience. For identity and access management, it is a critical point of competitive differentiation for today’s businesses. Besides the known and widely discussed value of lowering support costs, what…
-

How Sweet is Your Identity and Access Management (IAM) Suite?
Time to reconsider your identity and access management suite tooth. A common identity and access management (IAM) decision-making theme in many organizations seems to focus on selecting a “Suite” of products, but there is some movement in the corporate world to think of creating an identity ecosystem where multiple brands of products may be introduced…
-

Why Identity and Access Management is an Information Security Best Practice
Good habits make for information security best practices. When the CISO of a large organization calls and starts the conversation with “you’ll never guess why I’m calling”, usually I do have a pretty good idea of why they called. Something bad has already happened. Even though organizations claim to know the best security practices, it…
-

In a Services World Customer Success Teams Build Customer Loyalty
Customer success teams work toward a common a goal. My previous blog mentioned customer success teams in cultivating an effective support community. Customer success teams were also identified in developing customer loyalty and empowering customers, and building strong relationships without much detail. This blog focuses the critical role customer support teams perform in your business.…
-

ServiceNow Knowledge15 Looks to a Service Management Future
ServiceNow Knowledge15 focuses on fast easy enterprise-grade. In watching Frank Slootman, ServiceNow CEO and the Knowledge15 keynote speakers, you really do glimpse the future. The future of "Everything as a Service." For most enterprises, service management represents the state of operations in 2020. For some, particularly small and medium sized business, service management represents operations…
-

Killer Skills for an Identity and Access Management (IAM) Project
Red hot identity and access management skills. While working with a variety of companies who strive to improve their identity and access management program, I find that the most successful organizations have resources involved throughout the project that possess unique skills. It takes more than just IT project management and leadership skills to be an…
-

An IT Security Culture Deters State Sponsored Cyber Attacks
Time to develop a security culture. In previously criticizing the Anthem breach, I focused on preventative technologies. Clearly, identity and access management (IAM) makes cyber attacks difficult to launch. Equally crucial, IAM systems enable rapid remediation. They provide controls to automatically decommission compromised accounts, orphaned servers and passwords. During the Dropbox credential spoof, I highlighted…
-

Building a User Community and Loyalty through Customer Support Services
Means “Use Your Community” In my previous blog, I wrote about the importance of hiring support professionals with strong communication skills. I indicated a support professionals’ written and verbal communication skills are as vital to successful support operations as their technical capabilities. Particularly, your support staff’s verbal and written skills are essential when interfacing directly…
-

Chart Your Path to Identity and Access Management Success with Risk in Mind
Identity and Access Management charter. Identity and Access Management (IAM) projects are generally executed with a focus on delivering operational improvements, cost savings and eventual long-term security enhancements. Today, I am questioning whether you can afford to be satisfied with a "long-term" goal of security enhancements with your IAM program when organizations are being attacked…
-

HDI Conference Worth Trekking About
HDI Conference primer. Next week at the HDI Conference, the Help Desk Institute promises to host the hottest support industry party at LIGHT the hottest nightclub in Vegas. The party features Cirque du Soleil performers, incredible music, and certainly a one-of-a-kind evening. Does it get any crazier? In knowing I am about to “step across…
-

Customer Support Services Staffing Best Practices
Hire for optimum customer support services. As with any business, Avatier’s success depends on obtaining and keeping customers. You might have the best development, marketing, and sales teams on the planet, but none of that matters if you don’t lay the groundwork for long-term relationships with your customers. Whether you’re a director, support manager helping…
-

Identity Management Mitigates an Anthem Healthcare IT Breach
Anthem exposes healthcare IT vulnerability. When I initially read the Joseph Swedish letter taking responsibility for the Anthem information security breach, I found it refreshing. Upon finishing the message, I thought he should be fired. I mean. In a similar situation, who shouldn’t? More to the point, the third paragraph really got me: “Anthem’s own…
-

Announcing the Avatier Identity Management Support Wiki
Introducing the Avatier Identity Management Support Wiki You never know what you are going to get when walking into a new job…this is especially true when coming in as the leader of Technical Support. The interview process more than likely covers how fabulous the team is, how "mature" and "dependable" the product is and –…
-
The True Cost of Password Resets
User enrollment exposes a password manager’s true cost. Recently, I found myself in a discussion about the true cost of a passwords reset. Ironically, I was in a position where I had to defend spending more as part of a strategy to lower Help Desk requests and operational costs. In comparing software to software, the…
-

2015 Identity Management and IT Security Predictions
2015 Top identity management trends. 2015 ushers in the age of identity management authentication. With compromised systems reported by Target, Home Depot, EBay, Neiman Marcus, and Goodwill, 2014 is remembered as the "year of the retail breach". In 2015 every industry becomes a target, every identity a vulnerability, and every app a potential host. As…
-
The 12 IT Security Hacks of Christmas
Who’s putting coal in your IT security stocking? Although 2013 is remembered as the “year of the retailer breach,” in 2014, no industry is left out. With IT security breaches totaling over a half billion records in 2014, companies like Adobe, Ebay, JP Morgan Chase, Home Depot, AOL, NASDAQ and even Google joined the fold.…
-

What Will Your IT Security Get For The Holidays This Year?
IT Security gifts for the Christmas holidays. Happy Holidays! At least we’re all hoping they are going to be happy. With cybercrime and cyber terrorism on the rise, we’ll be lucky if we don’t get coal in our cyber stockings this year — especially if they already have cyber holes in them. According to a…
-

12 Identity Management Side Dishes to Avoid this Thanksgiving
Identity management recipes for disaster. Thanksgiving is a wonderful American holiday. It involves being thankful for family, football, shopping and eating. For an idea of American’s love for celebrating this holiday, forty-six million turkeys are stuffed, eighty million pounds of cranberries sauced, forty million green beans casseroled, twenty million pounds of potatoes mashed, and fifty…
-

Continuity and Automation Stop an IT Security Saga
Don’t let life put IT security in a twist. Monday, 11:55 PM: It’s been a long day for Bob. He worked all day as an information security professional, and then, he entertained a large group of friends all evening while watching Monday Night Football. Tuesday, 6:00 AM: Slow to wake and feeling a bit under…
-

Chiming In at the College of Healthcare Information Management Executives CIO Forum
CHIME 14 CIO Forum for healthcare IT executives and leaders. Last week I had the opportunity to participate in the CHIME 14 CIO Forum in San Antonio, Texas. This year the College of Healthcare Information Management Executives (CHIME) hosted over 800 industry professionals from all areas of the healthcare field representing the largest forum in…
-

Risk Should Point to Identity Management Investments
Identity management improves security at a lower cost. My numerous years of information security leadership experience at large organizations have helped me become a well rounded IT security professional. Therefore, you probably wonder why I spend so much time talking about identity management software over other security technologies. As hard as I try to stress…
-

The Dropbox Security Spoof and Password Reuse Caper
Dropbox security spoof exposes enterprise vulnerabilities. If you don’t know me, you may think I spend all my time writing about security breaches. Believe me I really would like to stop writing about them. I do hope organizations start paying attention. It just seems breaches are more pervasive. They are in the news more often,…
-

This Year’s Gartner Symposium ITxpo Had Risk Written All Over It
Gartner Symposium Booth 547. As the 2014 Gartner Symposium ITxpo draws to a close, I must admit it was one of the most stimulating, thought provoking symposiums I’ve seen. As advertised, the sold out show brought together over 8500 participants with 3000 CIOs to hear outstanding speakers from throughout the industry. What struck me, however,…
-

You need an Identity and Access Management solution if you deal with P.A.I.N.
Identity and access management manual processes. With all of the publicity around data breaches and information security issues affecting organizations today, I am still amazed to find companies who are willing to maintain antiquated identity and access management (IAM) processes. Maybe upper management simply isn’t aware of the operational and information security issues that exist,…
-

Go to the EDUCAUSE Conference Even if You Can’t
Attend the EDUCAUSE Conference online. Next week, the 2014 EDUCAUSE Conference showcases new instructional technology products, innovative educational services, and leadership best practices. With more than 250 exhibitors, four days of presentations, hot topic panels and a start-up alley, the event provides an opportunity to see how others address the key issues and challenges in…
-

“Do You Feel Safer?” 911 from an Information Security Perspective
Information security 911 preparedness. Thirteen years after one of the most horrific terrorist attacks on America, I have to ask myself "do I feel any safer?" Like you, I’m sure, the answer is "no." On the other hand, the risk I feel now has less to do with a physical attack and more to do…
-

For the Gartner ITxpo, Does the Early Bird Really Get the Worm?
Check out Avatier at the Gartner ITxpo to capitalize on innovation. I never do today what I can put off until tomorrow. My wife is just the opposite. With the Gartner ITxpo already just a month away, she suggested I provide a preview of what looks good. Today, in late August. Clearly, you can see…
-

Information Security and IT Leadership Business Accountability
IT leadership get aligned. In my last article, I discussed the need for IT leadership to start transitioning accountability to the business, but I primarily focused on security-related aspects of this transition. In this article, I highlight broader IT-related culture and process changes that can help organizations begin to deliver greater capabilities by engaging with…
-

UC Berkeley Web-Based Password Manager Examination
Web-based password managers. As you know from my blogs, I am an opponent of cloud single sign-on and password management services. At least at this point in time, I cannot think of a worse idea. What I am about to say will not always be true. It is true today. Any enterprise managing identities and…
-

Who Needs HIPAA HITECH Anyway?
The Formula 1® HIPAA privacy rule. A short while ago, someone stole the medical records for Michael Schumacher, the severely injured Formula One race car driver, and put them up for sale on the Internet for 60,000 Swiss francs. So far, no tabloid has picked them up. I’m not sure what they would pay for…
-

Think Broader than the “A” in IAM Identity and Access Management
Identity and Access Management (IAM) applies to more than just accounts. From working with various organizations, it is interesting to listen to differing perspectives about what capabilities identity and access management should encompass. Some people continue to believe that identity management only applies to accounts and access. This thinking limits operational and security improvements and…
-
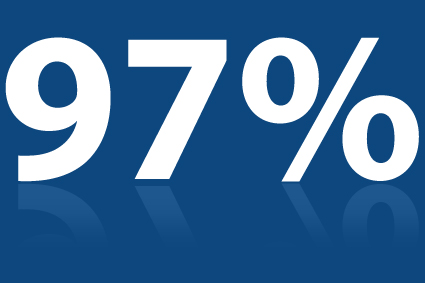
97% Customer Renewals for Avatier Identity Management System
Customer Renewal Rate. Recently, I was fortunate to work on the Why Avatier web page. My role was small in terms of the content I contributed. Yet, the impact reveals our company’s heart and soul. It’s the drive behind what we call business focused user-centric innovation. Before I started, I knew we had wildly successful…
-

Avatier Spins Off IT Security Consulting Company
At last, fixed-price IT security services. Last week we announced the launch of the IT Security Consulting Company, a spinoff of Avatier. We are using the expertise of this new group of consultants to provide services in all areas of information security including Identity and Access Management. Initially, we will be concentrating on sixteen areas:…
-

Identity Management Already Crossed Geoffrey Moore’s Latest Chasm
With identity management, business users were always the focus. When Geoffrey Moore, first wrote his book, "Crossing The Chasm" in 1991 it became an instant success among marketers, and remains so today. They resonated with the deep gap in customers and companies who are willing to try any new technology and those who felt they…
-
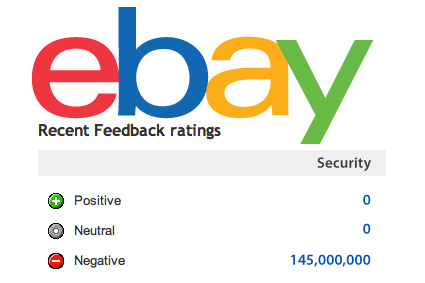
EBay Privileged Account Management Auction
eBay privileged account management feedback. I must confess. I am a little surprised by the media’s response and coverage of the eBay information security breach where hackers gained access to the personal data of 145 million customers over a four month period. During this time, cyber criminals accessed a database containing customer names, their email…
-

EDUCAUSE Security Professionals: Meet Me in St. Louis, Louie
At the EDUCAUSE Security Conference, the force is strong. The 12th Annual EDUCAUSE Security Professionals Conference 2014, drew from two audiences this week in St. Louis. Over 400 security staff, IT staff, privacy officers, and others from the higher education community with an interest in security and privacy were there in force—and a multitude of…
-

ITSM Solutions and IAM Solutions Are Not Mutually Exclusive
At last an ITSM IAM shopping cart. As ITSM professionals soak up the knowledge from ServiceNow’s Knowledge14 conference, it is interesting to see how the service management and identity management worlds are beginning to converge. Gone are the days when IT solutions only addressed specific target capabilities without meeting an organization’s greater needs. Now, identity…
-

Building a Great Identity Management Company From The Inside Out
Avatier identity management company values. You’ve probably heard the story about the guy walking down the street next to a building under construction. "What are you doing?" he asked the first bricklayer. "Laying bricks," he replied sullenly. "What are you doing?" he asked the second bricklayer. "Building a stone wall," he replied smugly. "What are…
-

The Heartbleed Security Flaw, Cloud Identity Management, and Avatier Company Statement
Heartbleed does not affect Avatier Customers. The problem with being right is that it often happens at the expense of someone’s detriment. Consider for a moment… when was the last time you said, “I told you so” after something positive occurred? Over the last month, I blogged on the security risks of duplicating identities in…
-

The ABCs of Avoiding Cloud Identity Management Fraud
Simplifying cloud identity management. I recently read the Better Business Bureau Names "BBB Top Ten Scams of 2013” and I thought to myself if such a distinction existed for B2B software and services, it would have to go to cloud identity management companies. To better clarify, it should go to cloud identity management companies who…
-

The 2014 HDI Conference and Expo Resembled a Sardine Can
The 2014 HDI Conference was packed. Over 2300 IT service and technical support professionals squeezed into the 2014 HDI conference and expo this week in Orlando. There were clearly two sides to the event: thoughtful motivation and mind expansion mixed with practical information from Expo exhibitors. On the conference side, five great speakers captured the…
-

Attend the HDI Conference with an Identity Management Focus
Avatier Booth 424 With the 24th Annual HDI conference and Expo nearing, I thought it would be wise to remind everyone about the importance of thinking holistically when choosing solutions that can help improve service desk operations. While a variety of ITSM solutions are on display, there will also be a focus on identity and…
-

A Shamrock Debunks Three Single Sign-On Software Myths
SSO lucky! When I tell people I work for an identity management company, a common response I receive is “Oh, you mean single sign-on?” For this reason, I have come to believe single sign-on or SSO is the “cola” of IT security lexicon. I say this because similarly SSO is often used as a catchall…
-

Avatier Packs Major Identity Management Changes into AIMS 9.5
Liftoff! This month the company launched the latest version of its Avatier Identity Anywhere (AIMS) providing several significant additions. AIMS 9.5 now includes SMS self-service password reset, a new patented approach to increased IT store intelligence, and revolutionary risk mitigation throughout. Enterprise Password Management AIMS’ Password Management module now features SMS two-factor authentication without requiring…
-

2014 RSA Conference Three Big Easy Wins
Security engagement. Some equate the annual RSA Conference to the Lollapalooza of information security events. I don’t always agree with this premise. However, this year’s conference was exceptional. Perhaps it’s San Francisco or maybe the times we live in. This 2014 RSA Conference did not disappoint. It delivered a full week of pomp, regalia and…
-

How an Identity Manager Stops Edward Snowden Administrators
Privileged whistleblower. Since Edward Snowden’s release of over 1.7 million classified NSA documents, trusted identities and privileges require re-examination. While opinions regarding Snowden range from traitor to Noble Prize winner, his actions delivered a wake up call to IT leaders. As an IT security professional, whether you support or abhor Snowden’s actions, you must take…
-

Why Your IT Security and Swiss Cheese May Have a Lot in Common
Cyber crime target. As if sustaining your own IT security data breach wasn’t enough, Target is now looking at the very real possibility that the attackers hacked their way in using access credentials stolen from an…wait for it…environmental systems contractor. Investigators from the Secret Service, which is leading the investigation, recently visited the offices of…
-

Organized Cyber Crime Target
Cyber criminals target retailers. Perhaps you saw the report by the US security firm iSight Partners concluding the stolen customer data now reaches as many as 110 million Target consumers. According to the report, the cyber crime began in Texas stores. Customer data was collected for over two weeks. And, the information was immediately sold…
-

Identity Management and IT Security Practices to Prevent Target-like Cyber Theft
IT security alerted. Last Friday near the end of day I thought I would speak to one of our engineers about this blog topic. Coincidentally, 5 minutes into our conversation, he received an alert indicating unusual resource consumption on our blogging server. Upon examination, someone accessing our login page from a server in New Jersey…
-

Gartner IGA Magic Quadrant Revealed
The Identity Governance and Administration Magic Quadrant. It’s Gartner time again. As a respected member of the information security community, I am certain you had an alarm set to notify you as soon as the Gartner Identity Governance and Administration (IGA) magic quadrant was released. After all, how can you possibly make an informed decision…
-

2014 Identity Management and IT Security Predictions
Top trends. Identity Management Predictions 2014 just started and the coming year signals a new era. In 2014, trends beginning around 2009 take shape to become the norm. Gone are the days of blind trust in privileged accounts, lackadaisical governance and the outsourcing frenzy. On the bright side for IT Security professionals, 2014 looks to…
-

Have A Hacker Over For The Holidays
Cyber Carol ‘Twas the night before Christmas and all through the house, many creatures were stirring while holding a mouse. Their stockings were hung by computers with care, in hopes that their breakins soon would be there. It turns out you don’t really need to invite a hacker over for the Holidays… they’ve invited themselves.…
-

Gartner IAM 2020 Predictions: Attributes Are Now "How We Role"
Role Based Access Control. Over the holiday I caught a flight. If you spend much time at the airport, I hope you take advantage of the TSA PreCheck. It’s marvelous and what a difference in terms of your experience. With the program, you pre-screen so airport personnel instantaneously know the risk you pose. For travelers,…
-

Gartner IAM 2020 Predictions: Identity Intelligence Finally Gets A Brain
Smart IT risk management. Recently on my way home from work, I stopped at a grocery store for a few dinner items. I knew what I needed so I was able to quickly navigated to the checkout line where I waited. Let’s recount the experience… Strategy. Execution. Bottleneck. For reasons unknown to me, the wait…
-

Gartner IAM Conference and Gartner IAM 2020 Predictions
The identity management future. Avatier is completely energized by the 2013 Gartner IAM Summit. We concluded the event by attending a Los Angeles Kings hockey game with over 20 fellow attendees for drinks, a catered spread and unbelievable dessert bar. Our suite offered a great chance to have more in-depth conversations than experienced on a…
-

NEW PHASE IN AVATIER GROWTH
Avatier LANDESK Partnership. Today we announced a tremendous new partnership with LANDESK Software. It is our first OEM relationship and represents a dramatic new growth phase for Avatier. LANDESK will be using our innovative self-service password reset tool as part of their LANDESK Service Desk in their Password Central product. Our enterprise password manager will be integrated…
-

Put the BUSINESS in your IT Service Catalog
IT service catalog like shopping. IT Service Management is a hot topic for many CIOs as they strive to improve operations, and implementing a Service Catalog helps the business and IT understand what services they truly provide to the business. Unfortunately, many organizations only focus on an “IT” Service Catalog rather than thinking holistically of the…
-

Why Role Mining Adds Tremendous Value to Identity Management Automation
Strategic access entitlements. Most companies on the verge of an identity and access management project face the challenge of mining roles to determine appropriate access for their workers. Even if an organization is not planning on implementing a complete role-based access control (RBAC) model, they should still identify some set of core birthright entitlements that can…
-

THE VIRTUAL VOYEUR
Attendance recommended. Participation a must. I’m not there and I should be. Time is money and I don’t have enough of either. So what’s the answer? One of the nation’s top conferences has figured that out. EDUCAUSE, the premier IT conference for the education industry, is in full swing this week with over 400 educational sessions…
-

Avatier Identity Anywhere Scores Five Stars from SC Magazine
Empowering businesses at a lower cost. Avatier is pleased to announce that its Identity Management Suite v9 was awarded a five star product review from SC Magazine. The review highlights a number of key strengths and benefits, including flexible architecture, comprehensive data security protocols, self-service automation, and a well-designed user interface. And, according to the…
-

Only in Vegas? On-Board 4,500 People in Less than 90 Days through Identity and Access Management
Casino-style identity and access management. Imagine what it would take to securely on-board 4,500 people over three months. As the first member of the Las Vegas strip community to embrace and deploy identity and access management software, The Cosmopolitan of Las Vegas accomplished precisely that. How exactly did they do it? The Cosmopolitan implemented an…
-

Hail to Your Health: How Single Sign-On (SSO) Software Saves Lives
SSO lifesaver. The advantages of single sign-on software are well established — it makes it easier for users to remember passwords, reduces the number of help desk calls and the associated expense and strengthens overall identity and access management efficacy. These universal benefits are of value to organizations across industries. In the health care industry,…
-

Do your homework — Sun Identity Manager migration
Retire your Sun identity manager. Yes, most identity and access management (IAM) companies are trying to convince current Sun Identity Manager customers to migrate to a different product since it is near end-of-life. Migrating to a next generation identity management software solution would be a very smart decision because there are certainly major benefits to moving…
-

The Perpetual IT Audit: Hop Off the Hamster Wheel with Identity and Access Management Software
Identity and access management controls. Access certification audits are aggravating for everyone — gathering system entitlement information, explaining the process to approvers and then documenting exceptions to achieve compliance governance is an exhausting and time consuming process. If you happen to work in an industry that’s highly regulated, it’s likely that you’re perpetually in the…
-

It’s 10PM. Do You Know Where Your Information Security Just Went?
Information security exposed. The study published in May 2013 by Ipsos Mori on behalf of Huddle found that a whopping 38% of U.S. office workers admit to storing work documents on personal cloud tools and services, including Dropbox, Google Drive and Apple iCloud. A staggering 91% report that they regularly use personal devices to access,…
-

InfraGard Highlights Focus Needed to Improve Information Security
Information security best practices. During last week’s information security Midwest InfraGard SuperConference, the FBI stressed concern about the growing problem of intellectual property theft from the United States via espionage. China accounts for 90% of that espionage so it was no surprise to learn that China was in the news for stealing information. Since over $250…
-

Identity Management HD: The Trends and Shifts Driving Identity Management Software Innovation
Identity management holistic definition. Recently Avatier’s CEO, Nelson Cicchitto, delivered a presentation at the HDI Conference and Expo 2013 covering the operational and cultural mega trends driving innovation for the next generation of identity management software. The implications on the evolution of IT operations are significant and imminent. So what are these critical macro trends percolating…
-

A Call for Dynamic Forrester, IDC, and Gartner Analysts’ Identity Management Reports
One factor to consider. I am sure I am not the only one who has been in a role where I felt “pressured” to steer a product selection decision around a major analyst firm’s recommendation (i.e. Gartner, Forrester, IDC, KuppingerCole etc.). As an information security professional, this can be extremely frustrating because identity management security is…
-

Stopping the ‘Enemy Within’ with IT Risk Management Software
Self-service IT risk management. If ever organizations questioned the need for IT Risk Management Software, one simple statistic about cyber security cited recently in the National Law Review should change their minds: “According to Diligence Information Security, about 70 percent of security breaches are committed by employees.” Yes, those dedicated individuals who depend upon your…
-

How to Use Identity Intelligence to Identify the Good and Bad within Your Organization
Identity intelligence must-have. Security professionals, just like business professionals, need to do a better job at leveraging the data available to them to make the best decisions possible. In business terms, this is considered Business Intelligence and it is all about effectively translating the wealth of data produced throughout the business into meaningful and useful…
-

Spring Cleaning: What’s Skulking in Your Identity Management Software?
Clean out your legacy identity manager. Spring cleaning — it’s the time of year when you purge the clutter, clear the cobwebs, file the taxes and visit the dentist. It’s when you tackle all those unsavory tasks prowling in the back of your mind for months. While you’re at it, don’t forget about your identity…
-

Think about "Risk Management" when Outsourcing Information Security
Outsourcing information security risks. I have never been a huge fan of outsourcing information security, especially when security operations and vulnerability management are intermingled with infrastructure outsourcing deals. I have had first-hand experience at previous companies dealing with the risks of all aspects of outsourcing from selecting ITO providers, migrating from one provider to another…
-

7 Key Costs Areas to Investigate When Purchasing an Identity and Access Management Solution
The true cost of ownership. So you think Identity and Access Management (IAM) product licensing is your main financial concern with an identity management project…? Think again! Unfortunately, many organizations undergo a very shallow evaluation of total cost of ownership (TCO) when selecting a solution, and this results in unexpected costs that end up dooming…
-

There’s No Business like Your Identity Management Business
Starring business performance. Try singing the theme song from the movie “There’s No Business like Show Business” in your head without it sounding like Ethel Merman. If you’re of my generation or older — a generation that remembers the incomparable singer and her signature song — it can’t be done. Business success and security are…
-

Resistance is Futile: The End of Identity Manager is Near
Sun Identity Manager alternatives. One thing we know from history is that all things must come to an end, and for Sun Identity Manager that end comes roughly 14 months from now. It has been reported that the “path of least resistance” for replacing the “sun-setted” Identity Manager product will be Oracle’s version; however, just…
-

What’s Bigger than Identity and Access Management? IAM IT Automation is…
IT automation muscle. It is time to start thinking more holistically about the capabilities of identity and access management and IT automation solutions to reach the end-goal of true business automation. Technologists continue to have a siloed view of their specific needs when searching for IT solutions, but by taking a step back and looking at…
-

Harry Potter and the Gartner Identity Management Magic Quadrant
Riddikulus! What’s so "magic" about the Gartner Identity Management Magic Quadrant? The Identity & Access Governance Management Magic Quadrant was just released and it’s not a "wand waver" by any stretch of the imagination. And that’s the point. If you go with the Leaders in this quadrant, are you really getting any imagination, creativity, or innovation or are…
-

ISACA Cloud Security Blog
ISACA addresses critical issues head on. Cloud security continues to be a hot topic in the information security world, and a recent ISACA webinar reaffirmed the fact that identity management is more critical than ever as services shift from on-premise to cloud-based solutions. One particular presentation stood out during the ISACA webinar for the three aspects…
-

IT Service Management: Five Features of a Road Less Traveled
IT savings add up. There are many paths organizations could take to achieve optimal IT Service Management (ITSM). While the necessity of a refined process for ITSM may not be apparent immediately, its essential nature in handling Identity and Access Management (IAM) issues becomes glaringly apparent as the help desk becomes more saturated with requests.…