Category: Avatier
-

Avatier vs. Saviynt
Some IT security choices matter more than others. Make a small mistake in your employee training? You can fix that quickly with updated training. On the other hand, implementing an identity and access management (IAM) software solution that is a poor fit will make your entire program less effective. Use this short guide to Avatier…
-

How Do Avatier and SailPoint Compare?
Some choices matter more than others in effective cybersecurity. The choice you make regarding identity and access management (IAM) software is vitally important. If you choose a system that is a poor fit for your company’s budget, you are going to be stuck working around system limitations for years. Are Avatier and SailPoint On Your…
-

Avatier vs. Oracle Enterprise Single Sign-On
In your single sign-on software research, Avatier and Oracle Enterprise Single Sign-On are two promising options. If you’re considering these products for your shortlist, how should you think about comparing them? Use our product comparison guide to identify which solution is better for you. 1) Avatier vs. Oracle Pricing: What Are The Pricing Structures? Some…
-

Avatier vs Micro Focus Access Manager
With Avatier vs. Micro Focus Access Manager on your shortlist of security software solutions, making the right choice is difficult. Both products have their advantages. However, it is essential to choose an application that relates to your technology and risk needs. To expedite your procurement process, use our feature comparison to make the right choice…
-

Avatier vs. ForgeRock Identity Platform
Comparing Avatier vs. ForgeRock Identity Platform for your company? Making a smart choice in identity and access management software is difficult. Make the wrong choice, and you will lose productivity and face a higher security risk. To help you weigh advantages and disadvantages, review our product comparison between Avatier and ForgeRock. 1) Avatier vs. ForgeRock…
-

Avatier vs IBM Authentication Solutions
You’re looking at Avatier vs. IBM Authentication Solutions for your company. How do you make a smart choice? It’s true that IBM has an excellent reputation and many years in the technology business. However, it pays to take a more critical approach in evaluating Avatier and IBM’s approach to identity and access management. 1) Avatier…
-

Avatier vs CA Technologies
Considering a choice of Avatier vs. CA Technologies for your identity and access management needs? If you have already developed your shortlist for products, it is time to look at features and capabilities so you can make a smart choice. Specifically, you will see a comparison focusing on Layer7 SiteMinder vs. Avatier Single Sign-On. 1)…
-

MFA Support and How It Works
Your multi-factor authentication (MFA) implementation needs the right technologies to work effectively. Sure, you can cobble together a few different technologies and manually manage the process. However, that approach is a recipe for frustration and burnout. Instead, you need to choose software solutions that are flexible in terms of MFA support. How Avatier Approaches MFA…
-

Cut Through The AI Security Noise With 5 Simple Questions
Every year, we see new artificial intelligence (AI) breakthroughs. First, we saw AI triumph in chess. Next, AI has moved to success in other games like GO. Companies have noticed and have started to adopt AI. Research from IDG found that 41% of companies are currently using AI in some form. From an IT security…
-

Avatier vs Idaptive Application Services
You’re considering Avatier vs. Idaptive Application Services for your identity and access management needs. What are some of the key features and differences to keep in mind? To simplify your selection process, use our quick reference guide. 1) Evaluating The Single Sign-On (SSO) Value Proposition In its simplest form, a single sign-on solution makes life…
-

Avatier vs Ping Identity
Choosing a single sign-on (SSO) software solution for your company is tough. One way to simplify the process is to build a shortlist of solutions. For example, you might compare Avatier vs. Ping Identity. To support you in making the right choice, let’s consider how these two products compare. Each one has its strengths and…
-

5 Ways To Use Narrow Band AI Chatbot
What can weak AI, also known as narrow band AI, do for your cybersecurity? The answer might surprise you. You might be inclined to be skeptical of artificial intelligence because you assume it requires a team of specialists. Fortunately, AI technology has come a long way, and it is now much easier to implement. To…
-

Narrow band AI Chatbot
When was the last time you looked at chatbots? Your first impressions may have been disappointing. Maybe you heard about the famous Microsoft chatbot failure in 2016. The first generation of “narrow band” AI services certainly had problems. However, the industry is changing. Today, you can have access to already-trained and finely tuned chatbots to…
-
Ranking AI in Movies: The Good, The Bad, and the Buggy
Robots in the movies aren’t a new phenomenon. For nearly 100 years, on-screen plots have featured various levels of robot intelligence and the full range of heroes through villains. In the infographic below, we rank artificial intelligence in the movies. Find out how some of your favorite robot heroes compare to the most hated, evil…
-

Building Business Value with Employee Experience
Competition for talent has never been greater. Companies lobby new graduates and professionals alike to join their companies. Alas, much of that effort is wasted when there’s no follow-through to offer a compelling employee experience. Without the employee experience in place, your people will hold back at work and continuously look for better opportunities. Inside…
-

People Managers: How Chatbots Cut Down Your Admin Work
Your people managers spend too time much on administrative tasks. Every hour, they waste energy and resources that could be better spent on growing the business. Ignore this reality, and you’re going to fall behind your competitors. The High Cost of Managers Working on Administrative Tasks Will Surprise You Some amount of paperwork is inevitable…
-

Virtual Agents vs. The Help Desk: Which Option Is Best?
You’ve heard about virtual agents, AI, and machine learning, but the question is whether they’re ready for your company’s needs. Read on to learn a straightforward way to use both methodologies to deliver great service to your employees. How to Execute Routine and Complex IT Tasks Effectively As an IT leader, you need to provide…
-

Avatier Critical Vulnerability Resolved
Avatier has fixed a vulnerability regarding weak social engineered questions, however, you are NOT AT RISK if you require additional authentication, like Avatier SMS, email One Time Passcode (OTP), or any Avatier supported third-party MFA provider. WHAT TO DO: Avatier has a hotfix. Contact Avatier Support for an upgrade of your production systems or you can download the…
-

Avatier vs. RSA: Which Is Right For Your Business?
According to CSO, “Identity and access management is a critical part of any enterprise security plan, as it is inextricably linked to the security and productivity of organizations in today’s digitally enabled economy.” IAM technology covers the wide spectrum of identity authorization and user access protocols, including who can log in to your system, how…
-

Avatier vs. NetIQ: Comparing Identity and Access Solutions
IT staff is facing an increasingly complex digital landscape where it’s necessary to maintain high security while balancing wide-reaching digital access. There’s a mixed environment of local servers, clouds, and third-party hosts combined with multiple access points from workstations, remote access, and mobile device. Scale these access dynamics across your company to understand the complex…
-

Are You Using the Best CAPTCHA for Online Security?
CAPTCHA is the name for online tools that distinguish between humans and bots. You’ve likely used a CAPTCHA when filling out a web form, or the CAPTCHA may have authenticated you behind the scenes without you realizing it. Here’s what you need to know about how CAPTCHA helps online security. What Is CAPTCHA? CAPTCHA is…
-

Avatier vs. OneLogin – Which Identity and Access Platform Should You Use?
An aspect of IT security, Identity and Access Management (IAM) is an increasingly important area of technology that involves user authentication, categorical access based on user group, improved user productivity with SSO, and streamlined user provisioning. The implementation of IAM can have a significant impact on your business, including an improvement in security, reduced costs,…
-

7 Productivity Benefits of Using Containers
What’s in it for you to start using containers in your technology? That’s what you will find out from this post. First, let’s take a step back and define our terms. What Is a Container? The first image that comes to mind might be a shipping container on an ocean-going freighter. That is not a…
-

Identity Management Glossary: The 6 Terms You Need to Know
You’ve decided to improve your identity management system, but there’s one problem. You’re buried under an avalanche of confusing terms. When that happens, you will probably start to feel anxious. How do you make sense of what the identity management vendor is offering you? There’s no need to become an identity management expert yourself. The…
-

How to Save Time on Your Next IT Audit
Nobody wakes up in the morning and looks forward to participating in an audit. That is why you need to find ways to make the whole process less painful for your employees. Streamline the record keeping and user certification aspect of your next IT audit. Saving time on audits is one way to establish your…
-

Never Forget Your Password Again: How to Securely Manage All Your Passwords
Current estimates suggest that the average person has 27 discreet online logins. That’s a lot of passwords to remember. But in order to keep your passwords secure, they should be 16 characters long and contain upper and lowercase letters, numbers, and symbols. Unless you’re a prodigy, I doubt anyone can keep track of these different…
-

7 Reasons Single Sign-On Is Better Than Managing Passwords
Single sign-on, as explained in a previous Avatier article, “utilizes just one set of login credentials to access multiple applications. This type of authentication process is a response to the growing number of user accounts and the shift towards cloud technology.” Because the average number of passwords per person has grown from 6.5 in 2007…
-

Report on Identity Management Names Avatier a Leader in Innovation And Products
In an announcement today, Avatier’s cutting-edge identity access management software was named an Innovation Leader and a Product Leader in the KuppingerCole Leadership Compass Report titled “Identity as a Service: Cloud-Based Provisioning, Access Governance and Federation (IDaaS B2E).” Written by Martin Kuppinger, founder and principal analyst at KuppingerCole Analysts, the report studied and ranked 25…
-

Emailing Behaviors: Do Business and Personal Email Accounts Overlap?
Here at Avatier, we wanted to know what percent of people keep their personal email account separate from their work email. Rather than making assumptions about what the current email behaviors were, we ran an independent and anonymous survey. The infographic below reveals the insights on current email behaviors, including data breakdowns by gender, age,…
-

How to Fast-Track GDPR Compliance
What if an auditor walked up to your company next week and demanded evidence that you are compliant with General Data Protection Regulation (GDPR) rules? How would you respond? That scenario may well occur at companies in Europe and beyond starting in 2018. Computer Weekly, a U.K. technology publication, estimates that U.K. companies may face…
-

How to Reduce Hotel Administration Without Sacrificing Security
Introduction The rapid growth of Airbnb showed the hotel industry that competition is not only alive and well but also liable to appear from new areas. To achieve success in the hotel industry, you need more time to focus on customer service and marketing. Unfortunately, old-fashioned IT processes are standing in your way, even as…
-

Avatier Group Self-Service Eliminates your Enterprise Risk Management Cyber Security Exposure
It’s time to put the trusted group accountability in the hands of business owners, rather than IT. Avatier Group Self-Service lets business users request membership while workflow automation controls changes and applies cyber security software audit controls. Let business users request groups to add to your systems without impeding IT. Automate workflow and establish group…
-

Biometrics in Movies Sci-Fi Security
Facial recognition used to just be for science fiction. Eye sensors and voice scanners used to only be something we’d see in the movies. But these biology-based security systems from science fiction are no longer just futuristic dreams. They are now the reality of maintaining security. Let’s revisit some examples of biometrics in movies and…
-

Determine ROI with Avatier IAM Solutions’ Built in Cost Savings Calculator
Usually when companies are looking into purchasing Access and Identity Management solutions, it is ideal to analyze output value against allocated funds to figure out total cost savings. Rather than wasting time trying to budget complicated cost calculations, Avatier IAM solutions include a built in Cost Savings Calculator that can be used to determine and…
-

Reduce Help Desk Calls by 30% with Avatier’s Self-Service Password Reset Management Solution
Users have a multitude of passwords to recall, often due to the fact that password security requirements are not universally the same. There’s the simple go-to password, the slightly more complicated password, the one that passes most security requirements… and then there’s the password that’s asking for your social, first born child, the national anthem,…
-

HDI Conference & Expo Help Desk Case Studies
HDI Conference peer to peer learning. As far events go, the HDI Conference & Expo is fun. General speaking, security and IT professionals are a serious bunch. On the other hand, help desk professionals have a good time. Don’t get me wrong – It’s a broadening event. From analysts and salt of the earth operators,…
-

Gartner IAM Summit Defines Success
Identity and access management on display at Gartner IAM Summit The 2015 Gartner IAM Summit in Las Vegas focused on successful identity and access management deployments. Gartner defines successful as IAM solutions that are simple, business driven, and secure. Simple refers to a solution’s degree of difficulty related to it installation, configuration, implementation and maintenance.…
-
Contextual Learning an Identity and Access Management Configuration Differentiator
Contextual learning accelerates the value you receive from an identity manager. To lower costs, businesses seek configurable solutions over custom developed IT applications. Most IT organizations do their best to avoid customizing enterprise apps. Customizations tend to be costly while creating maintenance challenges. As a response, identity management vendors are providing greater configuration options. Areas…
-

New Identity Management for the Mobile Workforce Avatier Identity Anywhere (AIMS) 10
Identity management just got mobile. As the global leader and innovator of the most user-centric identity management software on the market, we are proud to announce at the Gartner ITxpo 2015 the release of the Avatier Identity Anywhere (AIMS) 10. As the newest and most powerful upgrade to our solutions used by millions of users…
-

Avatier Identity Management and Cherwell Software Strategic Alliance Makes ITSM and Enterprise Cloud Computing Better
Avatier announces a Strategic Alliance Partnership with Cherwell Software. Today, at the Cherwell Global Conference, we announced an incredible partnership with Cherwell Software™, a leading IT Service Management (ITSM) vendor, business and workforce enablement system. Our strategic alliance partnership with Cherwell ensures best practices are utilized in the design and implementation of the integration of…
-
Four Ways to Preserve Customer Loyalty During Call Volume Spikes
How you respond during stressful times makes a difference. Remember building sandcastles? Constructing the towers and driftwood drawbridges was a blast. That is, until the tide came in and unexpected wave swept the beach and water flooded the kingdom. Only having prepared a deep and expansive moat did the realm remain safe. For everyone else,…
-

In a Services World Customer Success Teams Build Customer Loyalty
Customer success teams work toward a common a goal. My previous blog mentioned customer success teams in cultivating an effective support community. Customer success teams were also identified in developing customer loyalty and empowering customers, and building strong relationships without much detail. This blog focuses the critical role customer support teams perform in your business.…
-

Building a User Community and Loyalty through Customer Support Services
Means “Use Your Community” In my previous blog, I wrote about the importance of hiring support professionals with strong communication skills. I indicated a support professionals’ written and verbal communication skills are as vital to successful support operations as their technical capabilities. Particularly, your support staff’s verbal and written skills are essential when interfacing directly…
-

Customer Support Services Staffing Best Practices
Hire for optimum customer support services. As with any business, Avatier’s success depends on obtaining and keeping customers. You might have the best development, marketing, and sales teams on the planet, but none of that matters if you don’t lay the groundwork for long-term relationships with your customers. Whether you’re a director, support manager helping…
-

Announcing the Avatier Identity Management Support Wiki
Introducing the Avatier Identity Management Support Wiki You never know what you are going to get when walking into a new job…this is especially true when coming in as the leader of Technical Support. The interview process more than likely covers how fabulous the team is, how "mature" and "dependable" the product is and –…
-

Chiming In at the College of Healthcare Information Management Executives CIO Forum
CHIME 14 CIO Forum for healthcare IT executives and leaders. Last week I had the opportunity to participate in the CHIME 14 CIO Forum in San Antonio, Texas. This year the College of Healthcare Information Management Executives (CHIME) hosted over 800 industry professionals from all areas of the healthcare field representing the largest forum in…
-
Improving Password Security Shouldn’t Be Rocket Science
Password security blueprint. It amazes me that, despite all the money being spent on security measures, from endpoints to data leak prevention to database security, the single largest vulnerability continues to be passwords. To be specific, 76% of all breaches over the past few years were based on weak or stolen password credentials according to…
-

This Year’s Gartner Symposium ITxpo Had Risk Written All Over It
Gartner Symposium Booth 547. As the 2014 Gartner Symposium ITxpo draws to a close, I must admit it was one of the most stimulating, thought provoking symposiums I’ve seen. As advertised, the sold out show brought together over 8500 participants with 3000 CIOs to hear outstanding speakers from throughout the industry. What struck me, however,…
-

For the Gartner ITxpo, Does the Early Bird Really Get the Worm?
Check out Avatier at the Gartner ITxpo to capitalize on innovation. I never do today what I can put off until tomorrow. My wife is just the opposite. With the Gartner ITxpo already just a month away, she suggested I provide a preview of what looks good. Today, in late August. Clearly, you can see…
-
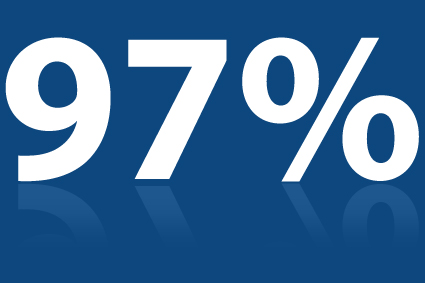
97% Customer Renewals for Avatier Identity Management System
Customer Renewal Rate. Recently, I was fortunate to work on the Why Avatier web page. My role was small in terms of the content I contributed. Yet, the impact reveals our company’s heart and soul. It’s the drive behind what we call business focused user-centric innovation. Before I started, I knew we had wildly successful…
-

Avatier Spins Off IT Security Consulting Company
At last, fixed-price IT security services. Last week we announced the launch of the IT Security Consulting Company, a spinoff of Avatier. We are using the expertise of this new group of consultants to provide services in all areas of information security including Identity and Access Management. Initially, we will be concentrating on sixteen areas:…
-

Building a Great Identity Management Company From The Inside Out
Avatier identity management company values. You’ve probably heard the story about the guy walking down the street next to a building under construction. "What are you doing?" he asked the first bricklayer. "Laying bricks," he replied sullenly. "What are you doing?" he asked the second bricklayer. "Building a stone wall," he replied smugly. "What are…
-

The 2014 HDI Conference and Expo Resembled a Sardine Can
The 2014 HDI Conference was packed. Over 2300 IT service and technical support professionals squeezed into the 2014 HDI conference and expo this week in Orlando. There were clearly two sides to the event: thoughtful motivation and mind expansion mixed with practical information from Expo exhibitors. On the conference side, five great speakers captured the…
-

Attend the HDI Conference with an Identity Management Focus
Avatier Booth 424 With the 24th Annual HDI conference and Expo nearing, I thought it would be wise to remind everyone about the importance of thinking holistically when choosing solutions that can help improve service desk operations. While a variety of ITSM solutions are on display, there will also be a focus on identity and…
-

Avatier Packs Major Identity Management Changes into AIMS 9.5
Liftoff! This month the company launched the latest version of its Avatier Identity Anywhere (AIMS) providing several significant additions. AIMS 9.5 now includes SMS self-service password reset, a new patented approach to increased IT store intelligence, and revolutionary risk mitigation throughout. Enterprise Password Management AIMS’ Password Management module now features SMS two-factor authentication without requiring…
-

Organized Cyber Crime Target
Cyber criminals target retailers. Perhaps you saw the report by the US security firm iSight Partners concluding the stolen customer data now reaches as many as 110 million Target consumers. According to the report, the cyber crime began in Texas stores. Customer data was collected for over two weeks. And, the information was immediately sold…
-

Identity Management and IT Security Practices to Prevent Target-like Cyber Theft
IT security alerted. Last Friday near the end of day I thought I would speak to one of our engineers about this blog topic. Coincidentally, 5 minutes into our conversation, he received an alert indicating unusual resource consumption on our blogging server. Upon examination, someone accessing our login page from a server in New Jersey…
-

Have A Hacker Over For The Holidays
Cyber Carol ‘Twas the night before Christmas and all through the house, many creatures were stirring while holding a mouse. Their stockings were hung by computers with care, in hopes that their breakins soon would be there. It turns out you don’t really need to invite a hacker over for the Holidays… they’ve invited themselves.…
-

Gartner IAM 2020 Predictions: Attributes Are Now "How We Role"
Role Based Access Control. Over the holiday I caught a flight. If you spend much time at the airport, I hope you take advantage of the TSA PreCheck. It’s marvelous and what a difference in terms of your experience. With the program, you pre-screen so airport personnel instantaneously know the risk you pose. For travelers,…
-

Gartner IAM 2020 Predictions: Identity Intelligence Finally Gets A Brain
Smart IT risk management. Recently on my way home from work, I stopped at a grocery store for a few dinner items. I knew what I needed so I was able to quickly navigated to the checkout line where I waited. Let’s recount the experience… Strategy. Execution. Bottleneck. For reasons unknown to me, the wait…
-

Gartner IAM Conference and Gartner IAM 2020 Predictions
The identity management future. Avatier is completely energized by the 2013 Gartner IAM Summit. We concluded the event by attending a Los Angeles Kings hockey game with over 20 fellow attendees for drinks, a catered spread and unbelievable dessert bar. Our suite offered a great chance to have more in-depth conversations than experienced on a…
-

NEW PHASE IN AVATIER GROWTH
Avatier LANDESK Partnership. Today we announced a tremendous new partnership with LANDESK Software. It is our first OEM relationship and represents a dramatic new growth phase for Avatier. LANDESK will be using our innovative self-service password reset tool as part of their LANDESK Service Desk in their Password Central product. Our enterprise password manager will be integrated…
-

EDUCAUSE the Future of Instructional Technology, Identity Management & IT Security
Ahead of the class. EDUCAUSE 2013 was no disappointment for the team at Avatier. When it comes to information technology innovation, education is always at the forefront of applied methods, exploration, experimentation and leadership. Although EDUCAUSE is eye opening in terms of its enormity, identity management as it relates to education is no stranger to…
-

THE VIRTUAL VOYEUR
Attendance recommended. Participation a must. I’m not there and I should be. Time is money and I don’t have enough of either. So what’s the answer? One of the nation’s top conferences has figured that out. EDUCAUSE, the premier IT conference for the education industry, is in full swing this week with over 400 educational sessions…
-

GameStop Wins by Proving Identity Management Saves!
Identity management effect. Congratulations to our customer GameStop for their stellar performance in Q2. The Texas company is the world’s largest multichannel video game retailer, According to StreetInsider.com, GameStop Corp. (NYSE: GME) reported Q2 earnings per share better than analyst estimates. Revenue for the quarter came in at $1.38 billion and as of 2:30 ET…
-

Better Enterprise Risk Management: Keep Your Priorities Straight with Balanced Scorecard Software
Balanced scorecard alignment. If you’re in charge of information security risk management for your organization, you know that the process is a study in trade-offs. You have to deal with acute, urgent problems — happenstances that are disrupting workflow in the here-and-now. But then there are those chronic drags — costly inefficiencies, latent security vulnerabilities…
-

It’s 10PM. Do You Know Where Your Information Security Just Went?
Information security exposed. The study published in May 2013 by Ipsos Mori on behalf of Huddle found that a whopping 38% of U.S. office workers admit to storing work documents on personal cloud tools and services, including Dropbox, Google Drive and Apple iCloud. A staggering 91% report that they regularly use personal devices to access,…
-

InfraGard Highlights Focus Needed to Improve Information Security
Information security best practices. During last week’s information security Midwest InfraGard SuperConference, the FBI stressed concern about the growing problem of intellectual property theft from the United States via espionage. China accounts for 90% of that espionage so it was no surprise to learn that China was in the news for stealing information. Since over $250…
-

A Call for Dynamic Forrester, IDC, and Gartner Analysts’ Identity Management Reports
One factor to consider. I am sure I am not the only one who has been in a role where I felt “pressured” to steer a product selection decision around a major analyst firm’s recommendation (i.e. Gartner, Forrester, IDC, KuppingerCole etc.). As an information security professional, this can be extremely frustrating because identity management security is…
-

Cyber Security Solutions Begins with You
President Obama’s cyber call to action. In case you missed it, President Obama wrote an extraordinary editorial that appeared in last Friday’s Wall Street Journal, focusing on cyber security threats on America’s infrastructure. The article begins by describing a simulation of multiple cyber security threats focused on deploying malware on critical systems that operate transportation,…