Category: Access Management
-

Eliminate Security Risk by Automating Group Management through Avatier Group Requester
For companies with thousands of users, it can become quite difficult to manage and group all of their user accounts. All it takes is for one employee with the wrong set of access controls to pose a serious security threat which can put your company in jeopardy. Avatier’s Group Requester offers an innovative solution as…
-

Determine ROI with Avatier IAM Solutions’ Built in Cost Savings Calculator
Usually when companies are looking into purchasing Access and Identity Management solutions, it is ideal to analyze output value against allocated funds to figure out total cost savings. Rather than wasting time trying to budget complicated cost calculations, Avatier IAM solutions include a built in Cost Savings Calculator that can be used to determine and…
-

Verizon Data Breach Investigations Report and Recommended Security Controls
Best practices for security controls Verizon’s 2016 Data Breach Investigations Report analyzes exploitation data collected last year. Not surprising, the distribution of incidences are similar to the previous year. The top 10 vulnerabilities still account for 85% of successful exploits. With automated attacks yielding incredible success, new vulnerabilities come out daily. With 95% of attackers…
-

HDI Conference & Expo Help Desk Case Studies
HDI Conference peer to peer learning. As far events go, the HDI Conference & Expo is fun. General speaking, security and IT professionals are a serious bunch. On the other hand, help desk professionals have a good time. Don’t get me wrong – It’s a broadening event. From analysts and salt of the earth operators,…
-

Uncovering and Recovering from Medical Identity Theft
Medical identity theft bites. I’m often advising others on medical identity theft. (May I add— more than I would like.) They for some reason equate my enterprise security career with protecting their personal health information (PHI). Timely detection is critical for thwarting medical identity theft. To do so, act immediately if you suspect someone spoofed…
-

The Force Awakens and the Gartner Identity Governance & Administration Magic Quadrant
May the force not mislead you. The Gartner Identity Governance Magic Quadrant was released and why did I stand in line? The Identity Governance & Administration (IGA) Magic Quadrant is not “new” by any measure of nonfiction. It goes without saying. The Leaders in this quadrant represent the status quo. As far as a solution,…
-

Extended Enterprise Security Risks Countered by Access Management
No end to extended enterprise security risks Management of assets, access requests, and user identities continues to change. No longer are employees the only ones accessing enterprise systems. No more are desktop computers and laptops merely used. A gamut of professionals engage multiple organizations. They use their own equipment to cross-different firewalls. They may even…
-

2016 Cyberthreat Defense Report Points to Identity and Access Management as Essential to Controlling IT Security Risks
When IT security fails, blame the users. The Cyberthreat Defense Report shares among the IT security community information on how organizations are fairing. Of the 1,000 survey participants, 40% were from North America, 30% from Europe, 20% from Asia Pacific, and 10% from Latin America. For respondents, 40% were senior executives; 25% focused on security…
-

Principles of Access Management Control
Remove unauthorized users automatically Access management involves effective management of all users’ and their enterprise access. Enterprise access management encompasses suppliers and providers as well as employees. Too often, organizations wait for a security incident before deploying sufficient access management controls. According to the recently released Forrester report, Understand The State of Data Security and…
-

Passwords to User Provisioning Progression
The password to provisioning exchange Help desk password resets are a costly and unnecessary IT operation. Manual processes are vulnerable to spoofing and they don’t scale. Enter enterprise password management, which enforces strong passwords for elevated security. It also frees up technical staff so IT can focus on more important aspects of their job. An…
-

Top 10 Information Security Worst of 2015
Information security under assault While 2014 became known as the "Year of the Information Security Breach," in 2015 privacy got thrown out the window. Fueled by success, cyber criminals were more sophisticated. They used better tools and exploited bigger targets with greater frequency. In response, IT organizations are evolving to view information security not just…
-

Gartner IAM Summit Defines Success
Identity and access management on display at Gartner IAM Summit The 2015 Gartner IAM Summit in Las Vegas focused on successful identity and access management deployments. Gartner defines successful as IAM solutions that are simple, business driven, and secure. Simple refers to a solution’s degree of difficulty related to it installation, configuration, implementation and maintenance.…
-

How IAM Makes ITSM Better—And Why They Belong Together
Add self-service IAM to your ITSM ticketing system. The goal of the IT organization is to create and protect business value. The "create" element seems widely understood; the IT service management function demonstrates value through the support and delivery of high-quality, cost-effective services that enable the business to meet their goals and objectives. The better…
-

EDUCAUSE Annual Conference Universities and Colleges in Need of Self-Service Security
EDUCAUSE Annual Conference self-service password management security At this year’s EDUCAUSE Annual Conference approaches, information security is principal. At universities and local community colleges, ensuring student privacy is so paramount. It is now included in many institutions’ value pitch. They should. According to the 2014 Identity Theft Resource Center Breach Report, Education made up 15%…
-

Gartner ITxpo Showcases Identity Management Prevention Controls
Identity management takes center stage at this year’s Gartner ITxpo. The Gartner Symposium ITxpo tends to be broad and scattered with numerous IT security and risk management solutions. Generally, at the Gartner ITxpo, participants do not naturally see the connection between identity management and information security. At this year’s 2015 ITxpo, the roadmap to security…
-

Four Stages of Identity Management User Provisioning Automation
Take on user provisioning automation. We often tend to want it all and we want it now. Lost in this mindset is time and activities required to reach fruition. Similarly, I see this with identity management. Customers seeking vendors in the earlier stages want it all. They also assume they should have it all on…
-

MLB Steps Up to Identity Management Big League
Major League Baseball ushers in a new era of cheating. Baseball, known as America’s Pastime, reflects our national identity, culture and values. The 1967 Major League Baseball (MLB) World Series featured the St. Louis Cardinals. The Series remains one of my earliest memories. On a tree swing in the backyard, I listened to the game.…
-

Avatier Identity Management and Cherwell Software Strategic Alliance Makes ITSM and Enterprise Cloud Computing Better
Avatier announces a Strategic Alliance Partnership with Cherwell Software. Today, at the Cherwell Global Conference, we announced an incredible partnership with Cherwell Software™, a leading IT Service Management (ITSM) vendor, business and workforce enablement system. Our strategic alliance partnership with Cherwell ensures best practices are utilized in the design and implementation of the integration of…
-

Top Identity Management in the Cloud Enterprise Applications
Most frequently requested enterprise cloud apps Let’s all agree. Identity and access management is core to IT security. Administration of software access and an individual’s credentials embody fundamental IT operations. Today, user management requires governing access to cloud and enterprise applications alike. Experts project global SaaS revenue to top $106 billion next year. This number…
-

NSA Map Shows Chinese Government Cyber Attacks on U.S. Targets
Over 600 reported cyber attacks since 2010. In the movie, Tucker: The Man and His Dream, Jeff Bridges plays Preston Tucker. As an entrepreneur, Tucker failed in 1947 to change the automotive industry. As a visionary, he succeeded in advancing automobile design, manufacturing and safety. In one scene, Tucker delivers an impassioned speech to investors.…
-

IT Support Shifts to Self-Service Employee Empowerment
IT support transparency Today’s enterprise IT support organizations and help desks are experiencing a shift in the way technologies are developed, deployed and consumed. As with identity management, all applications and systems are evolving faster than ever, with new cloud-based solutions emerging to replace on-premise software of generations past. User expectations aren’t far behind; a…
-

Eight Identity Management Practices for Stopping State Sponsored Cyber Attacks on Washington
Identity management defends against state sponsored cyber attacks. Last week Leon Panetta spoke at the Gartner Security Summit. His topic related to preventing cyber attacks in 2020. The irony was not lost considering four days prior. The Department of Homeland Security (DHS) announced our government’s largest security breach. Initially, ABC News reported four million employee…
-

Speeding Up the Gartner Security Summit
Gartner Security Summit Keynote Leon Panetta The Gartner Security & Risk Management Summit 2015 in Washington DC was no snooze fest. Quite the contrary. It’s just I don’t usually plan for security threats five years in advance. I’m engaged today. With the event infogram, "By 2020, 25% of global enterprises will engage the services of…
-

From Overhead to Profit Center: How Identity Management Customer Service Is Evolving
User empowerment through customer self-service options. Embedded wiki content and training videos along with effective customer self-service are critical elements to developing a positive, powerful customer experience. For identity and access management, it is a critical point of competitive differentiation for today’s businesses. Besides the known and widely discussed value of lowering support costs, what…
-

How Sweet is Your Identity and Access Management (IAM) Suite?
Time to reconsider your identity and access management suite tooth. A common identity and access management (IAM) decision-making theme in many organizations seems to focus on selecting a “Suite” of products, but there is some movement in the corporate world to think of creating an identity ecosystem where multiple brands of products may be introduced…
-

Why Identity and Access Management is an Information Security Best Practice
Good habits make for information security best practices. When the CISO of a large organization calls and starts the conversation with “you’ll never guess why I’m calling”, usually I do have a pretty good idea of why they called. Something bad has already happened. Even though organizations claim to know the best security practices, it…
-

In a Services World Customer Success Teams Build Customer Loyalty
Customer success teams work toward a common a goal. My previous blog mentioned customer success teams in cultivating an effective support community. Customer success teams were also identified in developing customer loyalty and empowering customers, and building strong relationships without much detail. This blog focuses the critical role customer support teams perform in your business.…
-

Killer Skills for an Identity and Access Management (IAM) Project
Red hot identity and access management skills. While working with a variety of companies who strive to improve their identity and access management program, I find that the most successful organizations have resources involved throughout the project that possess unique skills. It takes more than just IT project management and leadership skills to be an…
-

An IT Security Culture Deters State Sponsored Cyber Attacks
Time to develop a security culture. In previously criticizing the Anthem breach, I focused on preventative technologies. Clearly, identity and access management (IAM) makes cyber attacks difficult to launch. Equally crucial, IAM systems enable rapid remediation. They provide controls to automatically decommission compromised accounts, orphaned servers and passwords. During the Dropbox credential spoof, I highlighted…
-

HDI Conference Worth Trekking About
HDI Conference primer. Next week at the HDI Conference, the Help Desk Institute promises to host the hottest support industry party at LIGHT the hottest nightclub in Vegas. The party features Cirque du Soleil performers, incredible music, and certainly a one-of-a-kind evening. Does it get any crazier? In knowing I am about to “step across…
-

Identity Management Mitigates an Anthem Healthcare IT Breach
Anthem exposes healthcare IT vulnerability. When I initially read the Joseph Swedish letter taking responsibility for the Anthem information security breach, I found it refreshing. Upon finishing the message, I thought he should be fired. I mean. In a similar situation, who shouldn’t? More to the point, the third paragraph really got me: “Anthem’s own…
-

Cyber Liability Insurance Puts a Large Hole in the Corporate Wallet
Cyber liability costs. I was talking with a friend the other day and the cost of cyber breaches came up. Not so much the loss of reputation (which everyone faces), and the loss of sales, (which many face) and the loss of jobs (as Target executives faced)—but the cost of liability insurance assuming there is…
-

2015 Identity Management and IT Security Predictions
2015 Top identity management trends. 2015 ushers in the age of identity management authentication. With compromised systems reported by Target, Home Depot, EBay, Neiman Marcus, and Goodwill, 2014 is remembered as the "year of the retail breach". In 2015 every industry becomes a target, every identity a vulnerability, and every app a potential host. As…
-
The 12 IT Security Hacks of Christmas
Who’s putting coal in your IT security stocking? Although 2013 is remembered as the “year of the retailer breach,” in 2014, no industry is left out. With IT security breaches totaling over a half billion records in 2014, companies like Adobe, Ebay, JP Morgan Chase, Home Depot, AOL, NASDAQ and even Google joined the fold.…
-

What Will Your IT Security Get For The Holidays This Year?
IT Security gifts for the Christmas holidays. Happy Holidays! At least we’re all hoping they are going to be happy. With cybercrime and cyber terrorism on the rise, we’ll be lucky if we don’t get coal in our cyber stockings this year — especially if they already have cyber holes in them. According to a…
-

12 Identity Management Side Dishes to Avoid this Thanksgiving
Identity management recipes for disaster. Thanksgiving is a wonderful American holiday. It involves being thankful for family, football, shopping and eating. For an idea of American’s love for celebrating this holiday, forty-six million turkeys are stuffed, eighty million pounds of cranberries sauced, forty million green beans casseroled, twenty million pounds of potatoes mashed, and fifty…
-

Continuity and Automation Stop an IT Security Saga
Don’t let life put IT security in a twist. Monday, 11:55 PM: It’s been a long day for Bob. He worked all day as an information security professional, and then, he entertained a large group of friends all evening while watching Monday Night Football. Tuesday, 6:00 AM: Slow to wake and feeling a bit under…
-

The Dropbox Security Spoof and Password Reuse Caper
Dropbox security spoof exposes enterprise vulnerabilities. If you don’t know me, you may think I spend all my time writing about security breaches. Believe me I really would like to stop writing about them. I do hope organizations start paying attention. It just seems breaches are more pervasive. They are in the news more often,…
-

You need an Identity and Access Management solution if you deal with P.A.I.N.
Identity and access management manual processes. With all of the publicity around data breaches and information security issues affecting organizations today, I am still amazed to find companies who are willing to maintain antiquated identity and access management (IAM) processes. Maybe upper management simply isn’t aware of the operational and information security issues that exist,…
-

Go to the EDUCAUSE Conference Even if You Can’t
Attend the EDUCAUSE Conference online. Next week, the 2014 EDUCAUSE Conference showcases new instructional technology products, innovative educational services, and leadership best practices. With more than 250 exhibitors, four days of presentations, hot topic panels and a start-up alley, the event provides an opportunity to see how others address the key issues and challenges in…
-

Take Leadership ACTION When Undertaking an IT Risk Assessment
IT risk assessment influence. No matter how mature an organization is with managing security, it is almost guaranteed that some facet of security can be improved or overhauled at any given time. So where do you begin? This is why performing IT risk assessments is a critical component of any security program. Everyone agrees that…
-
The White House Wants To Pass On Passwords. Can we?
It is very positive news that the government is focused on improving authentication and identity management beyond the old-school usage of passwords, a huge security flaw in any enterprise system. After all, a typical eight character password has 6.1 quadrillion possible combinations. So we can feel pretty safe, right? Wrong. Just three years ago, it…
-

UC Berkeley Web-Based Password Manager Examination
Web-based password managers. As you know from my blogs, I am an opponent of cloud single sign-on and password management services. At least at this point in time, I cannot think of a worse idea. What I am about to say will not always be true. It is true today. Any enterprise managing identities and…
-

Think Broader than the “A” in IAM Identity and Access Management
Identity and Access Management (IAM) applies to more than just accounts. From working with various organizations, it is interesting to listen to differing perspectives about what capabilities identity and access management should encompass. Some people continue to believe that identity management only applies to accounts and access. This thinking limits operational and security improvements and…
-
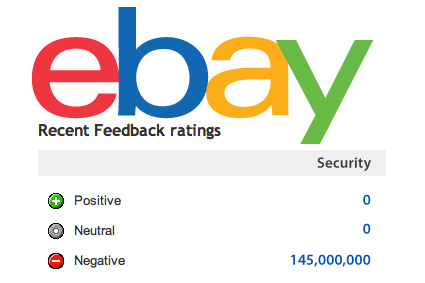
EBay Privileged Account Management Auction
eBay privileged account management feedback. I must confess. I am a little surprised by the media’s response and coverage of the eBay information security breach where hackers gained access to the personal data of 145 million customers over a four month period. During this time, cyber criminals accessed a database containing customer names, their email…
-

The Culture of Cloud in an Information Security World
Cloud information security cultural transformation. Working in the information security field, I obviously hear a lot about “the cloud” and its many security implications. There are definitely valid security concerns associated with cloud computing, but isn’t the entire industry of “information security” based on the concept of “securing information” no matter where it resides (including…
-

LANDESK Interchange 2014 an Educational Event for IT Experts
Learning that happens at LANDESK Interchange won’t stay in Vegas. With LANDESK Interchange 2014 a few days away, I could not be more excited about this year’s sessions, workshops and roundtable discussions. As someone involved in both education and marketing, I must confess I find conferences with an educational focus of greater value than their…
-

EDUCAUSE Security Professionals: Meet Me in St. Louis, Louie
At the EDUCAUSE Security Conference, the force is strong. The 12th Annual EDUCAUSE Security Professionals Conference 2014, drew from two audiences this week in St. Louis. Over 400 security staff, IT staff, privacy officers, and others from the higher education community with an interest in security and privacy were there in force—and a multitude of…
-

ITSM Solutions and IAM Solutions Are Not Mutually Exclusive
At last an ITSM IAM shopping cart. As ITSM professionals soak up the knowledge from ServiceNow’s Knowledge14 conference, it is interesting to see how the service management and identity management worlds are beginning to converge. Gone are the days when IT solutions only addressed specific target capabilities without meeting an organization’s greater needs. Now, identity…
-

The Heartbleed Security Flaw, Cloud Identity Management, and Avatier Company Statement
Heartbleed does not affect Avatier Customers. The problem with being right is that it often happens at the expense of someone’s detriment. Consider for a moment… when was the last time you said, “I told you so” after something positive occurred? Over the last month, I blogged on the security risks of duplicating identities in…
-

The ABCs of Avoiding Cloud Identity Management Fraud
Simplifying cloud identity management. I recently read the Better Business Bureau Names "BBB Top Ten Scams of 2013” and I thought to myself if such a distinction existed for B2B software and services, it would have to go to cloud identity management companies. To better clarify, it should go to cloud identity management companies who…
-

A Shamrock Debunks Three Single Sign-On Software Myths
SSO lucky! When I tell people I work for an identity management company, a common response I receive is “Oh, you mean single sign-on?” For this reason, I have come to believe single sign-on or SSO is the “cola” of IT security lexicon. I say this because similarly SSO is often used as a catchall…
-

How an Identity Manager Stops Edward Snowden Administrators
Privileged whistleblower. Since Edward Snowden’s release of over 1.7 million classified NSA documents, trusted identities and privileges require re-examination. While opinions regarding Snowden range from traitor to Noble Prize winner, his actions delivered a wake up call to IT leaders. As an IT security professional, whether you support or abhor Snowden’s actions, you must take…
-

Why Your IT Security and Swiss Cheese May Have a Lot in Common
Cyber crime target. As if sustaining your own IT security data breach wasn’t enough, Target is now looking at the very real possibility that the attackers hacked their way in using access credentials stolen from an…wait for it…environmental systems contractor. Investigators from the Secret Service, which is leading the investigation, recently visited the offices of…
-

Organized Cyber Crime Target
Cyber criminals target retailers. Perhaps you saw the report by the US security firm iSight Partners concluding the stolen customer data now reaches as many as 110 million Target consumers. According to the report, the cyber crime began in Texas stores. Customer data was collected for over two weeks. And, the information was immediately sold…
-

Identity Management and IT Security Practices to Prevent Target-like Cyber Theft
IT security alerted. Last Friday near the end of day I thought I would speak to one of our engineers about this blog topic. Coincidentally, 5 minutes into our conversation, he received an alert indicating unusual resource consumption on our blogging server. Upon examination, someone accessing our login page from a server in New Jersey…
-

Have A Hacker Over For The Holidays
Cyber Carol ‘Twas the night before Christmas and all through the house, many creatures were stirring while holding a mouse. Their stockings were hung by computers with care, in hopes that their breakins soon would be there. It turns out you don’t really need to invite a hacker over for the Holidays… they’ve invited themselves.…
-

Gartner IAM 2020 Predictions: Attributes Are Now "How We Role"
Role Based Access Control. Over the holiday I caught a flight. If you spend much time at the airport, I hope you take advantage of the TSA PreCheck. It’s marvelous and what a difference in terms of your experience. With the program, you pre-screen so airport personnel instantaneously know the risk you pose. For travelers,…
-

Gartner IAM 2020 Predictions: Identity Intelligence Finally Gets A Brain
Smart IT risk management. Recently on my way home from work, I stopped at a grocery store for a few dinner items. I knew what I needed so I was able to quickly navigated to the checkout line where I waited. Let’s recount the experience… Strategy. Execution. Bottleneck. For reasons unknown to me, the wait…
-

Gartner IAM Conference and Gartner IAM 2020 Predictions
The identity management future. Avatier is completely energized by the 2013 Gartner IAM Summit. We concluded the event by attending a Los Angeles Kings hockey game with over 20 fellow attendees for drinks, a catered spread and unbelievable dessert bar. Our suite offered a great chance to have more in-depth conversations than experienced on a…
-

Put the BUSINESS in your IT Service Catalog
IT service catalog like shopping. IT Service Management is a hot topic for many CIOs as they strive to improve operations, and implementing a Service Catalog helps the business and IT understand what services they truly provide to the business. Unfortunately, many organizations only focus on an “IT” Service Catalog rather than thinking holistically of the…
-

Only in Vegas? On-Board 4,500 People in Less than 90 Days through Identity and Access Management
Casino-style identity and access management. Imagine what it would take to securely on-board 4,500 people over three months. As the first member of the Las Vegas strip community to embrace and deploy identity and access management software, The Cosmopolitan of Las Vegas accomplished precisely that. How exactly did they do it? The Cosmopolitan implemented an…
-

At the Crossroads of Microsoft Active Directory, Identity Management and NERC Compliance Software
NERC compliance gatekeeper. Yesterday, many of you probably read about Entergy Corporation ETR announcing its plan to close and decommission the Vermont Yankee Nuclear Power Station. With the closing, Entergy explained the decision was driven by sustained low power prices, high cost structure and prospective for a heavily regulated wholesale electricity market. I couldn’t help…
-

Resistance is Futile: The End of Identity Manager is Near
Sun Identity Manager alternatives. One thing we know from history is that all things must come to an end, and for Sun Identity Manager that end comes roughly 14 months from now. It has been reported that the “path of least resistance” for replacing the “sun-setted” Identity Manager product will be Oracle’s version; however, just…
-

Harry Potter and the Gartner Identity Management Magic Quadrant
Riddikulus! What’s so "magic" about the Gartner Identity Management Magic Quadrant? The Identity & Access Governance Management Magic Quadrant was just released and it’s not a "wand waver" by any stretch of the imagination. And that’s the point. If you go with the Leaders in this quadrant, are you really getting any imagination, creativity, or innovation or are…
-
Keeping Your Ducks in a Row: Managing Governance Risk and Compliance
GRC software alignment. We all feel more comfortable and sleep better at night when we know that our ducks are in a row. We feel in control, confident, organized and secure. Where does this expression come from? Before traveling over land or water, mother ducks corral their young into manageable, straight lines. Any stragglers, escapees or…
-

Access Certification Software: It’s (Not) Too Good to Be True: Top 10 Features
Cost saving compliance. Today’s business world doesn’t work Monday through Friday from 9-to-5 and neither do those who threaten the compliance needs of businesses. Whether it’s an organization’s own employees accessing data for which they are not authorized or outside sources attempting to smear their good names, those responsible for identity and access management need…
-

IT Service Management: Five Features of a Road Less Traveled
IT savings add up. There are many paths organizations could take to achieve optimal IT Service Management (ITSM). While the necessity of a refined process for ITSM may not be apparent immediately, its essential nature in handling Identity and Access Management (IAM) issues becomes glaringly apparent as the help desk becomes more saturated with requests.…
-

Reduce Identity and Access Management Risks with a Holistic Needs Assessment
Assess technology and business needs. I’d like to think that I can figure out just about anything with technology, but from time to time I have to step back and think if my fresh research on a topic would truly be comprehensive enough to solve the organizational problem at hand. This is even more relevant in…
-

Gartner Identity and Access Management Summit Wraps Up
Gartner Identity and Access Management insights. It was quite a week in Las Vegas for the annual Gartner Identity and Access Management (IAM) Summit. While Avatier may not have been exactly a household name going into the conference, we certainly did our part to spread the message about the innovative ways the company is taking…
-
Avatier to Launch New Compliance Auditor Access Certification Software at Gartner
Audit any system, asset, network any time anywhere. The Gartner Identity and Access Management (IAM) Summit, one of the most influential events in the IAM industry, is just over one week away. Avatier has already released an announcement about their latest access certification software that it plans to launch at the show. Avatier, which will…
-

6 Key Ways to Fight the Identity and Access Management Battle Royale
IAM first line of defense. The Marine Corps motto, “Semper Fidelis” — Always Faithful — has always been revered by those who have served in “The Corps” as a pledge of brotherhood to one another. Whether in battle or in peace time, Marines have honored this sworn bond to stand united. But even this sworn…
-

IAM what IAM… But that’s Not All Identity and Access Management Is
Identity and access management crush. An interesting discussion came up recently on the Gartner Identity & Access Management XChange on LinkedIn. A participant asked for a breakdown of the elements that make up Identity and Access Management (IAM). A number of opinions were offered, most differing only slightly from the others. Perhaps the most different…
-

Assignment NOT Access Management Software
Access management software growth. It’s time for the IT and Information Security industries to start thinking in broader business terms when it comes to identity and access management software. “Identities” in businesses today require so much more than just security and IT-related resources, so why should enterprise-class solutions only focus on Access? What is truly needed is…
-

Cyber Security Threats and Attacks Put Economy at Risk
Cyber threats costs us all. It should come as a surprise to no one who follows the news that cyber security threats are on the rise in the U.S. and that the security of every business not innovative enough to thwart cyber attacks is at serious risk. The fact that employees remain points of vulnerability…
-

Getting Schooled on Access Management Software
Graduate to access management innovation. The incident is still under investigation, so school and law enforcement officials have yet to reveal whether this was a case of insider or external exploits. If it was internal, the breach once again underscores the necessity of a reliable identity access management software and brings into focus once again the…